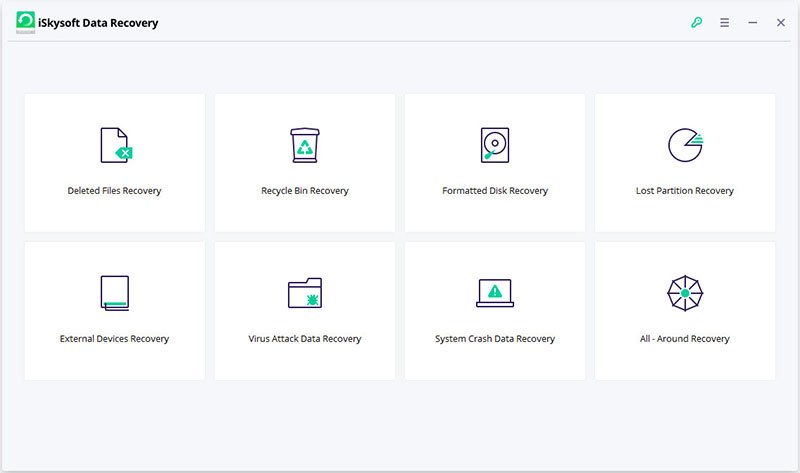
Choosing the best data recovery software can be a complicated task to do due to the similar services and features offered. The best way is by finding the reference and then comparing the services and features. While comparing the software, you can relate them with the important keys below.
Try to Get Software which Able to Recover Lost Data Caused by Any Problems:
When you are comparing the software, try to find whether the software is able to recover lost data by any causes or not, especially the one that you need to get your data back safely. This is also because there are many possibilities of why the data is lost or deleted. The data can be deleted because you want to delete it, removed by the Recycle Bin system, formatted system, system crash, virus attack, and lost partition. If the software is able to solve your problems, you can take it on your list. iSkysoft data recovery software can be included on the list because this data recovery software is able to solve your lost data problems.
Try to Get Software which Able to Recover A Variety of File Formats:
Your data consist of a variety of formats and some formats are hard to recover sometimes if it is lost or deleted. The solution of this problem is by finding a data recovery software which can recover any file formats from PDF, Doc, Docx, JPG, MP4, and MPEG to EML, DLL, CWK, XCF, FLV, and many others. As the result, the software helps to get any deleted and lost data in the form of a document, photos, video, audio, email, and other files. One of the reasons why iSkysoft data recovery software is included on the reference is because the software is compatible with those file formats and it means it reaches your achievement to get lost data back safely.
Try to Get Software which Able to Recover Data from Any Storage Device:
This is also an important consideration while finding data recovery software because you must have some devices to save data. It will be hard if you have to find a different tool for a different device when you lost the data. What you need is an all in one data recovery software which able to recover data from computer and any storage device. It hopes by using the software you can take the lost data no matter what the storage devices are including music player, digital camera, camcorder, or anything you have now.
Try to Get Software which Able to Repair the Crash System:
Sometimes, you face a worse condition where you are not only losing data but also the PC or computer because of a system crash. The good news, there is data recovery software which designed not only recovering lost data but also repairing the system crash. Just find out such software to solve your problem right way. As the result, you are not only repairing the PC system but also getting your lost data back. iSkysoft data recovery software is developed with the ability to repair a computer system crash problem. The software helps to create Windows Preinstallation Environment bootable media so you get access to the PC and the data back.
Try to Get Software which Supports A Variety of Systems:
You must have some devices in different operating systems. Due to this condition, you also need to find data recovery software which can support a variety of systems. Let say, the software has to be compatible with some popular Windows Operating System such as Windows 10, Windows 8.1, Windows 8, Windows 7, Windows Vista, and Windows XP. Moreover, the software also has to be suitable for Mac OS including Mojave, High Sierra, Sierra, El Capitan, Yosemite, and Maverick. If you read the detail of iSkysoft data recovery software, you might think that this software is suitable to solve your problem because it supports the operating systems above.
Follow the list above while finding the best data recovery software so you will not get lost and use the wrong software. The most important, the software can really solve your problem by taking your lost data back safely and repair the PC system. iSkysoft data recovery software meets the classification above because the software is not only used to recover data from the computer and any storage device, but it also used to repair the system. Even, there is a specific tool namely iSkysoft toolbox which able to boost the performance of mobile phone devices.
Summary: This article explains the things to consider when you are looking for the best data recovery software.
Read Also:
Featured Image: iskysoft.com