Whether you are a web developer or tester or a Project Manager, tools are always available at your disposal to help you. From our daily need tools like screenshotting tools to software testing tools we need a variety to make our work easier.
Looking to share an image? Take screenshot
Want to share a video? Use a screen recorder
Need to tell the developer, the code doesn’t work? Use a communication tool
From this to that, we need a ton of tools every day. Even you’re using one to read it! But which one is the best to use at a time is where one get stuck. And I’m here to help you with that!
Let’s find out which tool to use for your website and for what.
1. Testing : LambdaTest
If you own a website or web page or work for one, it is a must to perform its testing. LambdaTest in itself is a complete tool for your website to perform its cross browser testing (both manual and automation), visual screenshots testing, responsive testing, image comparisons, and a lot more.
With a pool of 2000+ browsers and device combinations, it helps you make sure that your website works perfectly in all browser and device combinations and provides a seamless experience to your users.
2. Code Editor: Sublime Text
Great websites need great environment and a code editor with well-designed, super efficient, and ultra speedy user interface to develop your code.
Sublime Text is on top to fulfill this need of your best code editor tool for your website. Sublime is unique in terms of Ease of use, easy shortcut keys and Eyes friendly user interface.
Developers spend 8-9 hours a day on code editor and Sublime text can prevent developers from getting frustrated. User-friendly and eyes friendly user interface is what one looks for while finalizing a Code editor tool and Sublime Text is all of them!
3. Design : AdobeXD
Adobe XD is a vector-based UX/UI design collaboration tool developed and published by Adobe Inc for designing and prototyping user experience for web and mobile apps for macOS and Windows.
XD supports vector design and website wireframing, and creating simple interactive click-through prototypes.
4. SEO: Uber Suggest
When it comes to SEO, no one can ignore Neil Patel and his toys. Uber Suggest is one of the top SEO tools in the current decade by Neil Patel.
SEO is what needs to optimize your website and make Google search friendly. Uber suggest can help in Keyword review whether it is for SEO or PPC, Keyword suggestion (from primary term to long tail phrases, you can get thousands of suggestion along with search volume, the competition, and even seasonal trends of that particular keyword), Keyword Difficulty and Competitive Intelligence. You can also assess your website against other competitors.
5. Design Mate: Zeplin
To build a website, you need to design it first and when it comes to it, Zeplin is Designer’s best friend. With all CSS details and minute information available in the design itself, it makes it easier to collaborate between developers and designers. It provides integrations with top tools like Slack, Trello and allows a user-friendly designing environment.
6. Analysis: SEMrush
SEMrush is an all in one tool for marketers. You can use it various analysis and help for your website. SEMrush has SEO toolkit, Advertising toolkit, Social Media Toolkit, Content Marketing toolkit, and Competitive Research toolkit to help you.
You can analyze your competitors, check which keywords they are ranking upon, monitor your keyword ranking, your website’s visibility, check which pages of your website are driving more traffic and a lot more.
As said SEMrush is all in one tool for Marketers.
7. Design Assistant: Canva
Canva is free to join and provides a vast variety of templates and graphics. It has everything that you need for an amazing design as a starting blogger, web designer, or app developer.
If you are promoting your website through social media, Canva can help you with images. Banners, posts, thumbnails, insta, snapchats, Google display ads, Facebook ads in standard required sizes. Equipped with so many tools, Canva is an awesome tool for marketers, web designers, artists, and social media enthusiasts.
8. Chat bot: Intercom
Putting a real-time chat bot is really a good option if you want your users and visitors of your website to connect to you any time. Intercom is undoubtedly the best tool to help you interact with your customers.
9. Screen Recorder: OBS Studio
Many times, we need to record our website’s animations for future reference or for forwarding it to some of our team members. OBS Studio is a screen recording tool along with various features like HD Streaming and recording. The best part about OBS studio is that there is no restriction upon the video length and it is very quick to set up.
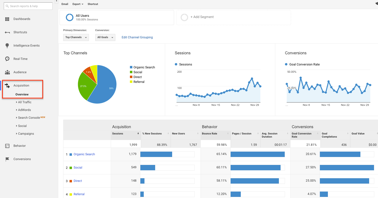
10. Analytics: Google Analytics
Analytics of visitors and user coming on your website or platform is key metrics to measure your company’s growth. You can set up custom channel from where you are getting traffic and can analyze which channel is performing good and which is not. Google analytics can help you play with numbers and take actions based on it. It’s a must-have tool if you are running your business online and have a website to showcase your products.
As a very famous saying goes:
We shape our tools and afterwards our tools shape us. – Marshall McLuhan
Hence, once we learn to use these tools, these tools can help us improvise and grow more. It is wiser to take help of the following tools for your website and increase your productivity. So, go ahead, try these tools and enjoy the fruits they reap.