Steam is a well-known name in the video gaming industry. It is a social gaming website, which allows you to play, buy, and discuss games. If you are using steam for some time, then there is a lot to know about it. Have you ever faced the Steam disk write error?
Are you looking for the solution to Steam disk write error windows 10? Are you unable to solve the issue? This article will help you with multiple solutions in order to remove the error. Go through the steps and enjoy an interruption-free gaming experience.
What Is The Steam Disk Write Error?
While you are updating or downloading any game you bought from the Steam Platform, you may face the Steam disk write error. At the time you are attempting to download or install a new game, this message can appear on the screen. You also can face the same issue when you are trying to update a game that you have installed earlier. In case your game needs an update, at the time of launching the game, the screen will show this error.
Reason For Steam Disk Write Error?
Whenever Steam is not able to download and save the data of the game to the storage drive of your computer during a new installation or an update. One of the messages mentioned below will appear on the screen,
- Any error occurred at the time of updating the game_title
- Any error occurred at the time of installing game_title
The steam disk write error can happen, when
- There are no defects on the hard drive.
- The Steam folder or drive is write-protected.
- There are outdated or steam corrupt disk files in the Steam directory.
- Your firewall or antivirus is blocking Steam from saving and downloading data.
Fixing Steam Disk Write Error
If you have encountered the steam error while downloading, error while installing, updating, or launching the Steam game and want to know the ways of fixing disk write error steam, here are the answers
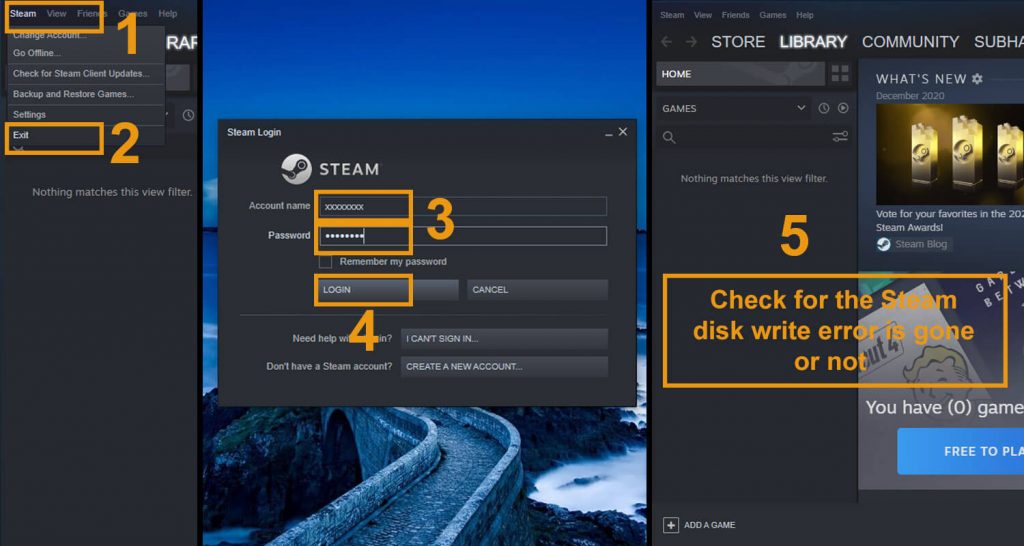
#1. Restart The Steam
- Open the Steam window
- Click the word “Steam” on the top-left corner
- The Dropdown menu will open
- For Windows, click on “Exit,” and for Mac, click on “Quit Steam.”
- Again open Steam.
- In case you have been logged out, log in another time
- Check for the Steam disk write error is gone or not
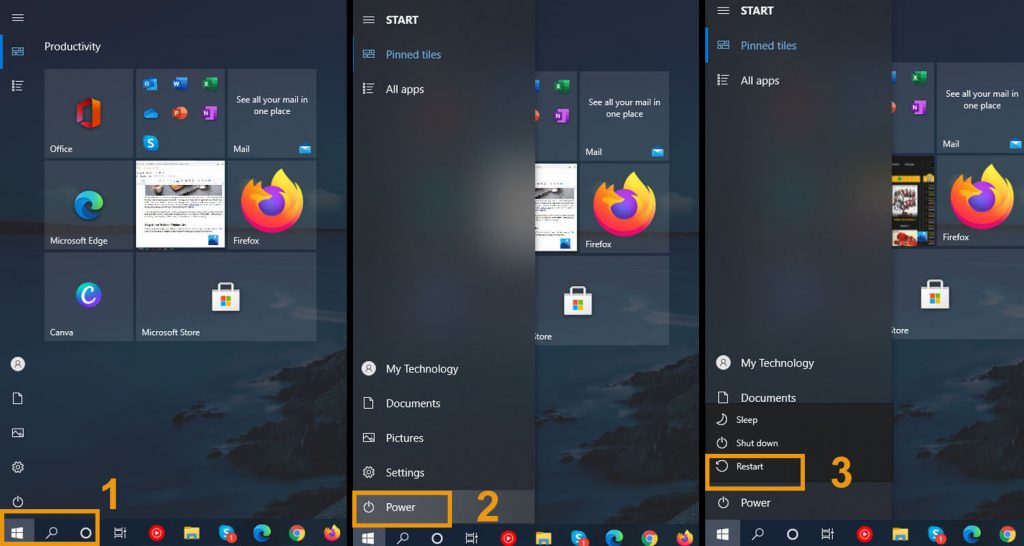
#2. Restart Your PC
- Click on the start icon
- Power Icon
- Restart
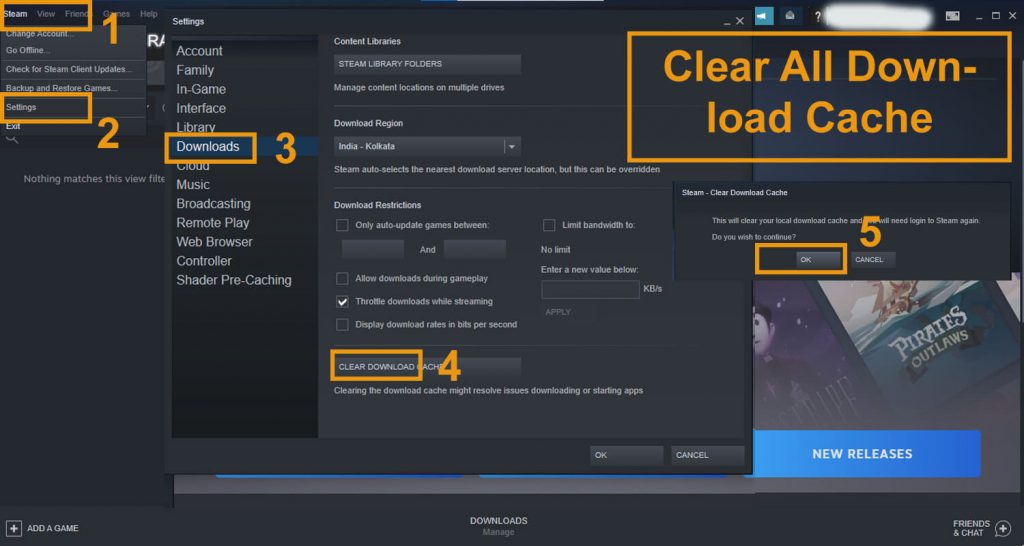
#3. Clear All Download Cache
- Open steam
- Go to “settings.”
- Click on “downloads.”
- Select the option “clear download cache.”
- Reopen and check if it is working or not
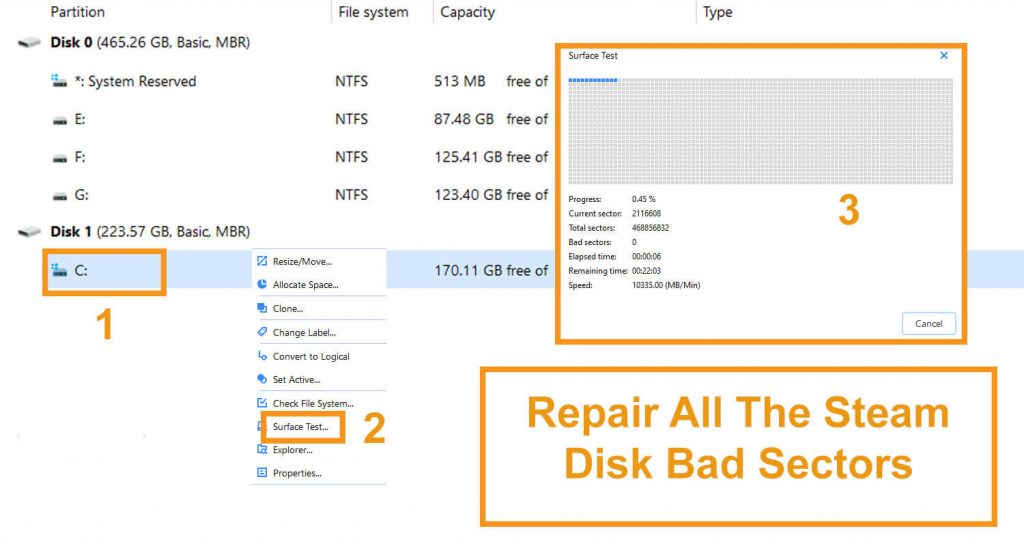
#4. Repair All The Steam Disk Bad Sectors
- EaseUS Partition Master to check bad sector
- Install it
- Click on the disk which you want to check
- Click “surface test.”
- It will red mark the bad sectors.
In case of any error, it is a good idea to replace the drive or clone it to another HDD apart from the steam disk write error SSD. You can take help from EaseUS Partition Master to replace the failing disk.
- After opening the EaseUS Partition Master, select the disk, which you want to clone.
- Click on “Clone”
- Select your destination or SSD/HDD whenever you want to clone it
- Click on “Next”
- Click on “Continue” to wipe out all data. If you have any valuable data, take a backup of it.
- Click on “Autofit the desk” or “Edit disk layout” or “Clone as the source.”
- Click on “Execute the operation.”
- Click on “Apply” to solve the steam disk write error
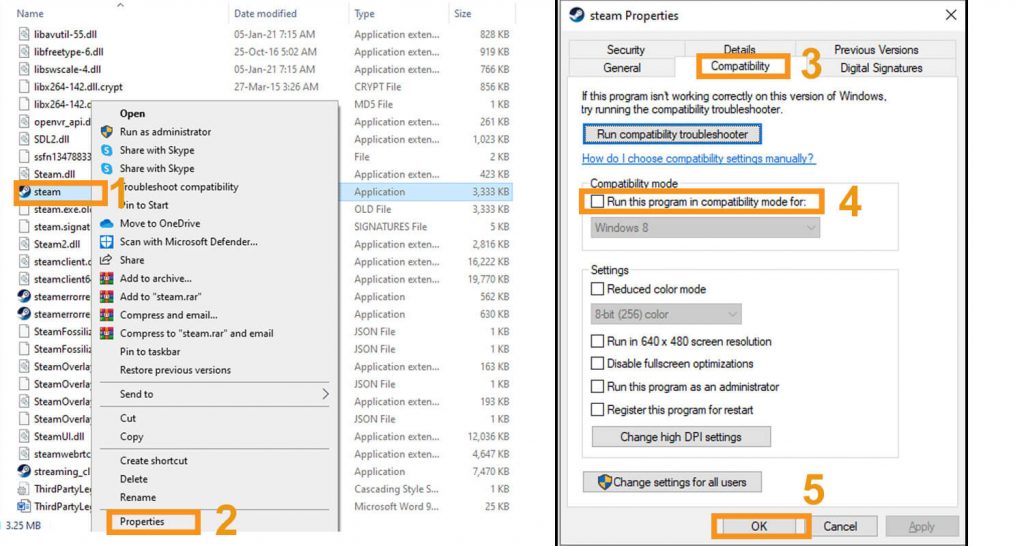
#5. Run As Administrator
- Go to your Steam folder
- Right-click on “Steam.exe”
- Click on “Properties”
- Select the tab named “Compatibility.”
- Click in “Run this program as an administrator.”
- Click on “Apply” then “OK.”
- See whether the Steam disk write error is solved or not
#6. Move The Game Folder
Sometimes transferring the game to a healthy drive can solve the issue. But here, manual transferring will not work. You can use EaseUS Todo PCTrans for transferring the file.
- Connect your computer with the destination drive
- Select the games that you want to transfer
- Now transfer them to the destination drive
#7. Confirm Integrity For Steam Game Files
- Reboot the system
- Launch Steam
- Click on the “Library” tab
- Right-click on the game that is causing the error
- Select “Properties”
- Click on the “Local Files” tab
- Click on the “Verify Integrity Of Game Files…..” button
- It will take some time to verify the game files
- Once the verification is done, try to install the updates and see if the Steam disk write error is showing or not.
#8. Remove The Write Protection From The Steam Drive For Steam Disk Write Error
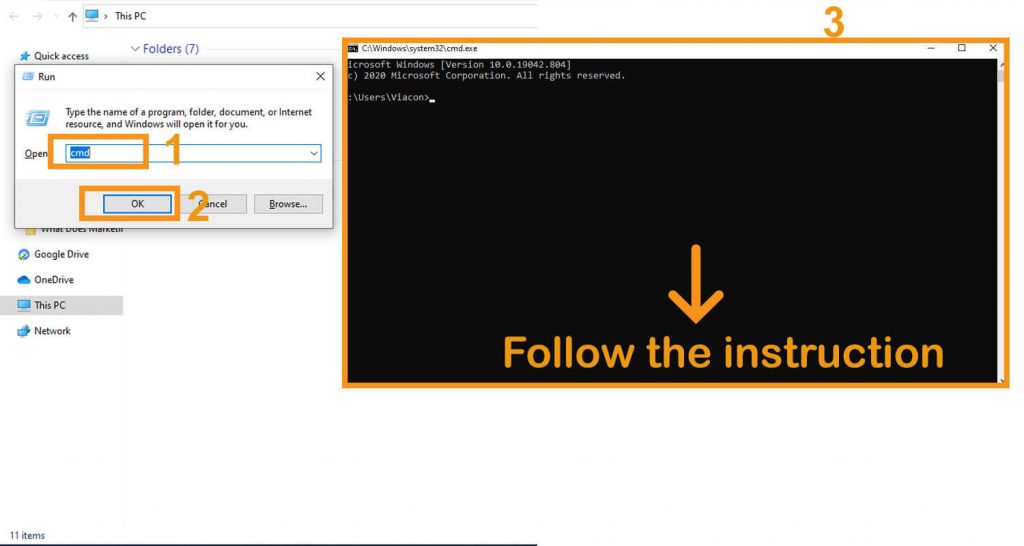
- Press “Win + R.”
- Type cmd
- Command Prompt will open.
- Type “disk part” there
- Press “Enter”
- Type “list disk.”
- Press “Enter”
- Type “select disk 0.”
- Press “Enter”
- Type “attribute disk clear read-only.”
- Press “Enter”
- After the write protection process is done, type “Exit.”
- Press “Enter”
- The disk part window will close.
#9. Some Other Fixes Of Steam Disk Write Error
Apart from all the steps mentioned earlier or techniques, there are two more ways to eliminate the Steam disk write error. You can uninstall Steam and reinstall it. In order to uninstall
- Go to “Control panel.”
- Open “Add or Remove programs.”
- Search for Steam and select it
- Click on the “Remove”
- After selecting the automatic option, click on “Next.”
- Click “Finish”
Once the uninstallation is completed, you can install it again. For installing Steam, follow the below steps.
- Visit https://store.steampowered.com/about/
- Click on “Install Steam”
- After the download is completed, click on “Open” or “Run.”
- Follow the on-screen instruction to install Steam.
- Open steam and log in.
Final Talk
Though you have tried and everything to resolve the issue, it is not working. You can seek help from Steam’s official support. Opt for the Steam support team. You also can visit the community forum of Steam for any further or additional help. Apart from the above-mentioned nine solutions of steam disk write error, if you know any other practical solution, do let us know.