Category: Technology
ContentRally is a leading source of reliable news and trending topics on Technology. Get hard-to-find insights and advice on Technology from industry-specific leaders.

Why Spy Phone Are Beneficial To Use?
Let us admit that spying on someone is a very difficult thing to do. Not every time you will be able to keep an eye on that person. But there is a way through which you can get most of the information about a person nowadays is through their Smartphone. Only you have to get to know about the phone calls and various text messages that come into that particular phone. It's not possible to look at another phone without him knowing that. But there is an application that makes it easy to know about your cheating spouses. The name of the app is the Spy phone and it is getting its popularity slowly. Only you have to install the app on that particular phone to get every information off that phone. So without further to do let's just look at the various details of this amazing application. Following Activities Would Be Tracked By Spy Phone: Here I am going to list out some of the main functions of this spy application so that you can use it accordingly. It will keep a record of the incoming and outgoing calls with the phone number. The actual time and date of the call will also be listed in the records. All the outgoing and incoming text messages will be tracked with the phone number it was sent and received. In this case, also that date and time will be recorded. Every 30 minutes, it will be sent the exact location of the mobile phone to the control panel so that you could know where the person is. It is also beneficial if the Smartphone is lost. When you visit many websites it will keep a record of it with the exact time and date of visiting. All the data that was tracked will be stored there 24/7 and whenever you want you can log in to see each and every detail and analyze it. Spy phone will use the phone internet to send the details to the central server. Not only for adults you use this app for your child so that they don’t go into the wrong ways. An average child over 5 years uses a Smartphone without knowing its benefits and disadvantages. So this application will allow you to look at the activities of the kid so that he/she cannot do some odd thing with the phone. As you know nowadays the adult content is destroying the mindset of the kids. Top Reason To Use Spy Phone: There are some valid reasons to use a spy phone to track someone's activity on their phone. The installation of this app is free and fast. It can be used on most Android phones. All the activity can be recorded such as phone numbers, incoming and outgoing calls. Whenever you log in to the website you will be able to access all the details. The 24/7 website is easily accessible. It also has the GPS tracking feature which will provide you with the exact location of the device. Further, there are some other activities which will help you to track others without facing any problem. Above written is an application through which you can spy on people easily. And record all the activities happening on their smartphones. A spy phone will help you to know the people surrounding you. it any be your wife, husband or kids but you can know about the things that they are doing in their life. So without thinking more use it and dig up the James bond inside you. Read Also : Best iPhone Spy Apps Without Jail Breaking 7 Essential Apps For Your Mac In 2018
READ MOREDetails
6 Tech Conferences You Don’t Want to Miss This Year
Technology has greatly transformed the way we do business. The benefits cut across all elements of productivity, from speed and efficiency to storage and connectivity. Networking and collaboration with like-minded cohorts play an important role in promoting the adoption of technology. The same can be achieved through Tech conferences, where attendees get the opportunity to raise their individual profiles and careers. According to the INC Magazine, technology conferences also offer a platform to learn, gather content, and share information. Learning is the greatest motivation for attending conferences. While at the conference, attendees can follow proceedings and share content through blogs, tweets, and live feeds. Every year, hundreds of technology conferences are held all across the world bringing together various stakeholders. According to My Business, here are 6 tech conferences and fairs you cannot afford to miss: 6 Tech Conferences 1. Consumer Electronics Show (CES) Las Vegas : January 9 – 12 This annual event is often seen as the showpiece and launchpad for cutting-edge technology and innovation expected to transform the world over the coming decades. The event is organized by the Consumer Technology Association (CTA) and brings together business leaders, thinkers, innovators, and tech enthusiasts from all over the world. Event Website: www.ces.tech 2. SXSW – Austin : March 9 - 17 This annual technology event takes place in Austin, Texas. The event offers professionals from various backgrounds an effective platform to learn and create business opportunities in technology, music and filming, and other industries. The 3-day disruptive event regularly attracts key speakers from large tech concerns like Google, IBM, and Facebook. Event Website: www.sxsw.com 3. CeBIT – Hanover : June – 11 - 15 The CeBIT event in Hanover, Germany ranks as one of the most important in the tech calendar. The annual event usually attracts over 200,000 people and mostly brings together businesses operating in the B2B value chain. Attendees have an opportunity to learn about new technologies and market trends shaping the business. Event Website: www.cebit.de 4. TechCrunch Disrupt, San Francisco, New York September 5 – 7 The TechCrunch events take place in different cities around the world, including San Francisco and New York in the US. The attendees include investors, tech enthusiasts, entrepreneurs, hackers, and business leaders. The annual event regularly attracts new and disruptive startups hoping to showcase their cutting-edge technologies to the eager world. Event Website: www.techcrunch.com 5. Web Summit, Lisbon : November 5 - 8 This event ranks as one of the largest tech conferences in the world. The event is held on a rotational basis in various global cities. In the past, the Web Summit has attracted names like Al Gore, Françoise Hollande, and UN Secretary-General Antonio Gutiérres. The stages featured include Content makers and contributions by leaders of leading global corporations like Siemens, Mercedes-Benz, and IBM. Event Website: www.websummit.com 6. Slush, Helsinki : December 4 - 5 The event is organized by Slush, a student-led, non-profit movement in Helsinki, Finland. The goal of the movement is to establish a global-scale startup community constituting business founders and investors. The organization also looks to inspire future business leaders and businesses. Event Website: www.sluch.org Conference Speaker Sean Seshadri : Sean Seshadri is a Financial Expert, Motivational Speaker, Educator, and Investor based in Florida. He is a graduate of the Weill Medical School of Cornell University. Sean holds a Doctor of Medicine Degree. His public speaking engagements have taken him to several places around the world, including major universities, business forums, and technology conferences. In the checkered world of business, Sean Seshadri is an authority in financial markets, options, stocks, and futures. He is the Founder and CEO of Lux Investments Intl, a hugely successful trading firm. Read Also: Is Polyester Stretchy? – Its Materials & Properties [Detailed Explanation] Top 6 Different Types Of Scarves Names And Its Benefits How to Thicken Chili – Tried and Tested
READ MOREDetails
Bitdefender Antivirus for Mac Review
When it comes to protection, you can choose very few select products for your Mac device. The reason is that there are only a few antivirus companies that have the configuration and programming best suited for protecting Mac computers. However, all companies will claim to provide all-around protection to your Mac notebook. The main question is how you can actually tell which one to trust. Bitdefender Antivirus for Mac is one of the best and most reliable antivirus programs that you can find. According to Andrea Marx who is CEO of AV-TEST, Bitdefender scores 100% in the arena of antimalware protection on all the Mac devices. Perfect protection for your Mac : Bitdefender promises to provide you with the best experience regarding both cybersecurity technology and affordability. It claims to give you the fully-fledged freedom to use Mac devices at their best. The latest update of Mac assures you against all the threats that are both common and rare to the Mac device. Bitdefender, with its multiple layers of protection, will prolong the longevity of your device. It is equipped with multilayer protection against all types of ransomware. Added to that, Bitdefender will provide you with a shield against any and all online threats. Using Bitdefender will drastically improve all of your online experiences. Often you have been plagued by advertisements that suddenly pop up while you are watching a video or playing some online games. Installing Bitdefender will prevent those advertisements to pop up and it will block them. It will grant you seamless viewing experience. It will also ensure that the performance and speed of your Mac improve drastically. But the best part is that Bitdefender is one of the few antiviruses that incorporate the goodness of cloud-based technology. Bitdefender will provide you with a constant guard against all the malicious attacks by cloud-based technology 24/7. Like much other mainstream antivirus software, Bitdefender offers a thirty-day free trial for all their products. Features Of Bitdefender Antivirus : Take a look at the specifications and functionalities that Bitdefender offers you: Bitdefender Shield: A specialty of Bitdefender is the Shield protection that is provided with it. From smaller threats to complex threats, Bitdefender will handle all the nitty-gritty of your security needs. The software is equipped with unique proprietary technologies that will automatically detect and eliminate all kinds of threats. All you need to do is to turn on the Bitdefender Shield and sit back. Time Machine Protection: One of the specialized features of Bitdefender Antivirus for Mac is Time Machine Protection. The feature that will automatically back up all your files saved in your Macbook and will provide protection from all types of ransomware attacks. This will also be extremely useful against ransomware that tries to encrypt and destroy all your personal and confidential data. Safe Files: TheSafe Files feature is a feature that will allow you to save all your files in a special folder. Keeping in this folder will ensure that your data will be protected from any kind of unauthorized changes. All you need to do is to add all the folders into its watch list. The applications that you will trust will only be allowed to access all these files that have been added to the watch list of the Safe Files feature. Blocking and removal of ads: No one likes spontaneous advertisements flying up in their programs. Even Macs can get nosy adware contaminations that redirect your browser and drive you up the wall. Bitdefender identifies and eliminates adware, noxious criminal projects, annoying toolbars, and other irritating program additional items so that you can make the most of your Mac. Super-Fast Scanning: Ironclad insurance is an extraordinary thing, yet it's far superior when it accompanies unrivaled speed and execution. Bitdefender consolidates exactness and speed, so you get ultra-quick outputs and the best identification rate in the business. Autopilot Feature: The new Autopilot has been designed as a Security Advisor and its purpose is to give you a more streamlined experience with your security. Its shrewd abilities imply that it can carry out security activities without hogging resources or bothering you with endless requests and notifications. Cloud-based security: The continual updates ensure that all your system remains protected by Bitdefender at the highest level of protection. However, viruses and ransomware get updated continuously too. In fact, the updates are designed only after the newer threats emerge. The latest threat that has emerged is in the form of cloud computing attacks. Bitdefender Cloud-based security advances to distinguish and take out e-dangers, wherever they may originate from, to give you continuous overall insurance. As the hard work is done in the Cloud, there's no delay in your Mac's performance, and your own data remains secure on your PC. Anti-Phishing features: With the rise of online transactions and more and more reliability on online banking, the threats to the online bank data and piracy are on the rise. Online scams are an especially dangerous thing that can liquidate all your life's savings within seconds. The anti-phishing technology from Bitdefender will help you to keep your device and personal banking information safe and secure from all the phishing attacks. It will automatically detect and block all the websites that mask as trustworthy banking sites. It will adeptly protect all your data like credit card details, passwords, net banking information, customer id, etc. Final Verdict : Seeing all the advanced features, the verdict is to go for this antivirus without any second thoughts. Tried and tested by all the experts all around the world, Bitdefender is the best antivirus that will serve the protection of your Mac device very well. All you need to do is to install and subscribe via the available online subscription. There is very little difference between the home use antivirus and commercial use antivirus. So go for it! Read Also : 7 Essential Apps For Your Mac In 2018 Top 10 Computer Security Mistakes
READ MOREDetails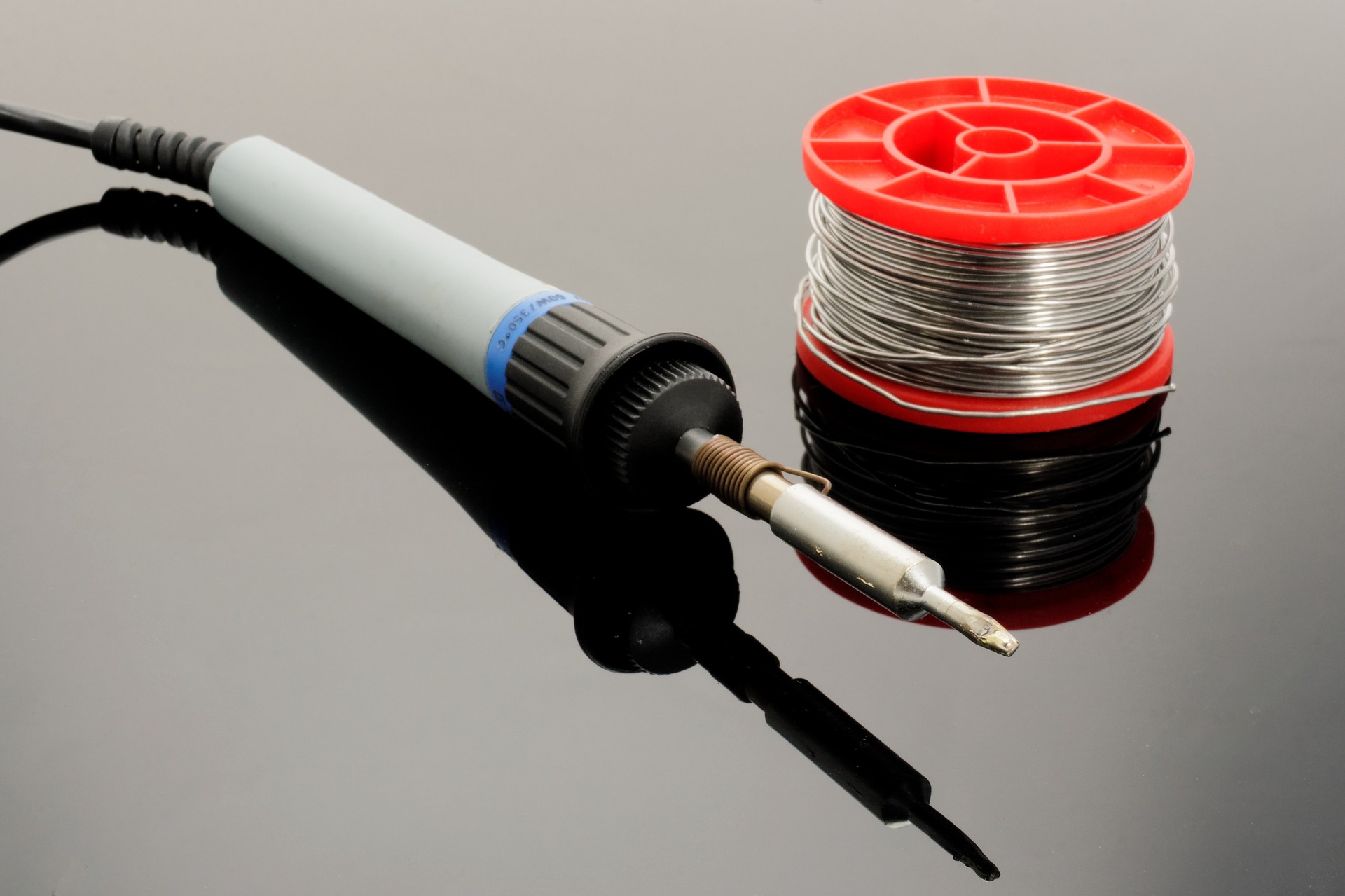
How to Use a Soldering Iron
Of all techniques and methods used to join surfaces, metal sheets, Iron, and other objects together, soldering is highly preferred because it does not cause any type of damage to the items being joined together. This is because the solder used to stick them together has a lower melting point than most metals and it offers durable yet reversible bonds between the items. In addition to that, although there are a few key differences between the two types of soldering gear used, they share a similar trait and they’re both easily operable, which we will discover more in this article What Is Soldering? There are several types of soldering using different filler metals called solder, but, they all use the same concept which is heating a filler metal between two items so that it melts and fills the seam between the two items. Soldering is done using either individually bought soldering gear, which allows you to choose the type of tool that is most suitable for the project you are planning to work on, or a soldering station which usually is a standard combination of a soldering iron and a power supply. Soldering Iron In order to learn how to use a soldering iron, one must first know its basic parts and the science behind its mode of operation. It is simply a tool that connects to a power supply, it consists of a handle that doesn’t conduct heat and a tip that heats up very quickly to high temperatures so it can melt the solder, it also cools down fast. To Be More Specific, The Main Parts Of Soldering Iron Are: Soldering tip: All soldering irons contain iron tips which are the only part that heats up; it doesn’t ooze out the solder as most people think, it simply heats the metals being joined so that when the solder is applied, it melts, but more often than not, the solder would stick on the tip. Luckily, most tips are interchangeable so, you can replace your tip in case of damage or in case you need a specialized tip to suit your uses; bear in mind that tips vary in size and shape, thus, they vary in their uses as well. Wand: The wand is the handheld part of the iron that the tip is attached to. It can be made from a large number of materials that poorly conduct heat or isolate it completely so as to prevent heat from the tip from transferring to the part where the wand makes contact with the skin. Inside the wand, there are wires and metal contacts that conduct and convert the electricity from the power outlet to heat. The contradicting functions of a wand are the reason why most people prefer to buy high-quality wands from renowned brands. Of course, there are other extras and accessories like brass sponges, cradles, and tip tinner which can be purchased individually or found in soldering stations which is actually one of the advantages of soldering stations; but, the two main parts will always remain the tip and the wand. Step 1: Safety First of all, before using a soldering iron, you must be familiar with standard safety precautions since the iron tends to get really hot; not to mention the fact that solder is literally molten metal. So, it would be smart of you to wear protective gear such as; safety goggles and protective gloves, because your fingers are most likely to come into contact with the tip during the first few times. You also should keep in mind to tie your hair and avoid wearing loose-fitting clothes. Moreover, it is preferable to work in a well-ventilated area since some types of solder contain lead which produces toxic fumes, it is also important to thoroughly clean your hands after handling lead-based material. Step 2: Preparing The Tip The tip should be regularly cleaned of any old solder because when old solder solidifies, it turns into a heat isolator due to oxidization resulting in a totally inefficient and highly wasteful soldering process. Not only that but also, slow heating means that you will have to hold the iron to the items being joined for a longer time; it would be highly inconvenient for you and very damaging for sensitive objects like PCBs. So, when the iron is fully heated, softly drag the tip against a sponge to remove old solder. You want to aim for a shiny tip. After cleaning the tip, you should “tin” the tip; to make it last longer and conduct heat better through newfound layers of solder. Same as above, on a fully heated iron, apply a little piece of solder and lightly coat the tip with tinner; then, immediately start soldering while cleaning and tinning the tip between every couple of joints for maximum conductivity and efficiency. Step 3: Actual soldering With your dominant hand holding the iron and the other holding a piece of solder, touch the area where the object comes into contact with the solder and hold it there for about a second then slide the solder underneath the tip while pushing the solder rod further according to how much solder you need. Then, make sure to pull back the solder first while holding the tip in position until all the solder melts; it usually takes about five seconds or less. Solder cools down fast so, you will not need to blow on the joint since it will only lead to a weak joint which can be identified by its oxidized, unclear, and grainy appearance. What you want to get is a smooth connection, not a lump. Finishing touches : After you’ve had enough soldering for the day, clean and in the tip again before you put it into storage, it helps increase its lifespan. As you may have noticed, soldering is not that hard of a task, it only requires soldering gear, steady hands, and concentration. So, go ahead, start soldering, and don’t be afraid to get creative. Read Also: Is Polyester Stretchy? – Its Materials & Properties [Detailed Explanation] Top 6 Different Types Of Scarves Names And Its Benefits How to Thicken Chili – Tried and Tested
READ MOREDetails
Top cloud security controls you should be using
Most organizations use at least some form of cloud storage, yet security issues are still a top concern. Data loss and security breaches are always in the news, with some of the most high profile data breaches to happen in 2018 so far including those that occurred at Reddit, Timehop, and FedEx. What this shows us is that even large companies can make mistakes that seriously compromise the security of their data. A 2017 survey conducted by Clutch revealed that while confidence in cloud storage security is high among small businesses, most are not doing enough themselves to protect their cloud storage. After all, cloud security requires involvement from the user, as well as the provider. We go over some of the top cloud security controls your business should be using to help ensure your data is adequately protected. Why do you need cloud security control? Every day, sensitive information continues to fall into the wrong hands. That’s according to Breach Level Index, as of August 2018. While cloud computing can be great for businesses, providing several benefits such as cost savings and data portability, it does come with certain information security risks. To protect your business against vulnerabilities, you need to put specific controls and standards into place. That’s where cloud security controls come in. They help to address, evaluate, and implement cloud security. They can include the following types of controls. Deterrent: These serve as a warning to potential attackers, warning of possible adverse effects if they were to proceed in their attempt, thereby helping to deter unlawful access. Preventative: These controls strengthen the system against attacks, protecting and managing vulnerable parts of the storage. Corrective: These help to reduce the consequences of an attack, which typically involves limiting damage. This could take place during or after the incident occurs. Detective: These controls will identify or detect an attack, and then respond to the incident. If an attack is detected, the detective control will signal to the corrective and preventative controls in an attempt to minimize damage. Using different types of controls will help to limit and prevent potential damage when using cloud storage solutions. What seems to be the problem? What businesses need to understand is that you cannot rely on your provider to do all the hard work. The issue is not that the cloud environment itself is insecure, but that customers are failing to configure their networks, applications, and data accurately. For instance, let’s take a look at what went wrong with Timehop. On 7 July 2018, the company was affected by a significant data breach that included email addresses, names, dates of birth, and phone numbers being taken. What was the issue? A cloud account that didn’t have multi-factor authentication. For Reddit, although they had two-factor authentication in place, their SMS-based authentication was not as secure as it needed to be. As for FedEx, the problem traces back to Bongo International LLC, a company bought by FedEx back in 2014, which had been storing sensitive client data on an open Amazon S3 bucket. The data had been available for public access for several years, having been collected from 2009 to 2012. Data can be put at risk in many different ways, so it’s essential to have the proper controls in place from the start. Find out what you are responsible for Many cloud services will offer some level of security. What companies need to do is find out exactly what they are responsible for when it comes to securing the data that is uploaded to the cloud. Ignorance is no excuse. Speak to your provider and find out which cloud security controls you are responsible for and what services they offer. Whatever tools are at your availability, make sure you use them all. Ultimately, you are responsible for securing your data, so take advantage of any security tools at your disposal, then make sure you take care of the rest. Limit cloud access A good way to reduce risk is to limit who has access to the sensitive information you are storing. Public cloud storage resources, such as Amazon’s S3 bucket, should not allow external access. Leaving SSH open is another common mistake. You should only allow those who must use the data directly to carry out their job to have access to the data. You can grant temporary access on an as-needed basis to any additional employees. Make the most of the identity and access control tools used by most major cloud providers, so you always know who has access to your data. When granting access, you have the option to limit what data someone has permission to access. Delegate appropriate permissions as needed and remove or disable accounts if an employee leaves the company. Keep your data secure One of the most common mistakes that companies make is to leave data unencrypted. You want to be sure that even if all other security measures fail, you have at least encrypted your data as a last measure of protection. While some providers offer encryption, companies should still use their own encryption techniques alongside these. Your decryption keys should remain within the company so that you can maintain control over these at all times. Learn from past mistakes Even large companies make mistakes when it comes to cloud security. You cannot merely rely on your provider to handle all aspects of security. Users need to ensure they are using current cloud security controls to ensure their data remains secure. The good thing is that we can learn from others’ mistakes. You can take extra precautions and implement certain controls and standards to improve security. Just make sure you pay attention to what is happening in the world of cloud security and update standards and controls accordingly. Read Also : What You Are Paying For With A Virtual Data Room Top 10 Computer Security Mistakes
READ MOREDetails
Top 10 Computer Security Mistakes
So you’ve gone out and purchased a brand new laptop, and now you have plans of using that laptop in the workplace. Well, for anyone who has experience running a company, knows that laptops can be conduits for spyware and viruses. Once data is being processed, thought must go into who is capable of stealing it, where they might store it, how they could archive it, and how valuable the data is to the company. Well, if you want to ensure you’re never in any unfortunate positions, then I suggest you check out my list of common mistakes most new computer users make. 1. Connecting to an Unsecure Network If the network is open, then it should be fine for you to connect to, right? I wouldn’t say that. You should always be suspicious of open networks, especially ones at hotels and airports. If it’s possible for you to connect to a network without using a password or agreeing to any terms, then there is a good chance you could be leading yourself into a trap. 2. Opening Attachments from Unsolicited Emails You want to check the content of your emails, if anything in it looks suspicious, or if the sender is asking you to do something that you do not feel comfortable doing then there is a good chance its spam. Check the sender, if you’re not familiar with the person, then try searching for the email on any of the major search engines. If you’re at your workplace, then consider contacting your email administrator for verification on whether or not the email is spam. 3. Using Common Passwords While the vast majority of people are wise enough not to fall into this trap, especially when signing up for services online, there are still many work colleagues that have a knack for using basic passwords, like their birthday or their username123. You’ll want to re-work your password by combining uppercase letters, numbers and uncommon symbols. If you chose London as your password, then you could rejig it to something like L0nd3N. Even though it isn’t the most complex password, it would be much more difficult for a hacker to guess. 4. Not Making Backups When it comes to archiving files, many end users make the common mistake of backing up data too infrequently. I can see how the lazy approach can be more comforting, but if your company files are that important to you, then you’ll want to ensure that they are backed up as often as possible, using a number of different mediums, such as the cloud, external hard drives, etc. 5. Leaving Your Webcam Enabled It’s a great idea for you to familiarise yourself with your webcam so that you can determine when it’s disabled or active. Hackers are very adept at hacking into your webcam, especially in the workplace, and they can even record meetings if you’re not careful. Covering the webcam with tape won’t do much since audio can still be recorded; it’s for this reason why you’ll want to ensure its disabled when not in use. 6. Searching the Deep Web The deep web, unfamiliar to most internet users, is the shady part of it, not accessible from the major search engines like Bing and Google. Work systems should be used for work only, there are many deep websites out there that will stick malicious code onto your computer and use that to track whatever you say and do. 7. Assuming Your Hard Drive Will Never Fail In this world, there are two different kinds of computer users, those who have lost computer files and those who will eventually lose computer files. You want to back things up as often as you can. You also want to think about alternative media, like using an external hard drive to save certain confidential data onto it. 8. Using a Suspicious Thumb Drive Everyone needs a place to store their work documents. If you’re in the office, it’s not uncommon for you to find a thumb drive lying around. My advice is not to use it, especially if you don’t know where it came from, that’s because there’s a good chance it could have a virus on it. 9. Using the Same Password across Accounts It’s very important that you make a habit of changing your passwords. It’s not uncommon for end-users to keep the same password for many years. That is something you do not want to do. For business-critical, sensitive data, you want to ensure that all passwords are changed at least once every three months. Make sure all your accounts have different passwords. Having multiple passwords for your many accounts reduces the chances of all your accounts being compromised. With the increasing amount of cyber-attacks, the age of your password, along with its length and complexity are far more important today. 10. Agreeing to Install Anti-Virus Software Have you ever visited a website that asked you whether or not you wanted to check your system for a virus? You may have asked how or why it knew you needed a virus scan. In most cases these prompts to install antivirus software are in fact attempts to install malicious software on your system. Read Also : Would Your E-commerce Website Pass The Cybersecurity Test? Here Are 3 Things You Could Be Doing Wrong How To Securely Wipe Your Confidential Data From A Hard Drive
READ MOREDetails
Top 8 Advantages Of Effective Web Design And Development
Quality web design tends to be a valuable investment. You need to have an effective Web Design And Development for some reason. Read on to find out more: 1. A good first impression It is beneficial to have a good first impression. The front of the website nowadays is literally your storefront. When a new client comes you always think about forming the best first impression of this web design company’s website, their website looks very impressive and professional. The same case should be present on your website. It should be such that it is an immediate reflection of the business, your personality as well as you. If the website is unprofessional then it could result in visitors not feeling welcome. It may also give the impression that the business you have is outdated. They will look somewhere else for services which you could have given them. You do not want this. 2. More visitors You do not only want clicks. You need visitors that will browse through the site and find out who you are. Some people will leave your website after simply glancing at it if it is a confusing website that does not have a good Web Design And Development. You need something special so that people will be interested and want to purchase your product or even service. Many fail to realize that website design plays a critical role in increasing the traffic figures for a website. An attractive design helps in keeping the audience engaged and reduces the bounce rate. This, in turn, helps SEO, as search engines like websites that have extremely low bounce rates. The Best Web Design Agencies play an important role in creating a fluid and attractive UI and UX to help brands engage, retain, and improve website traffic. 3. Stronger search engine ranking SEO or Search Engine Optimisation tends to be the optimization of one’s website so that one can get a higher ranking in today’s search engines. At the time that people search for a certain business and service, they search for key terms in these search engines. Looking statistically, users will visit those that appear first or second in their search. For those who have an outdated site, it does not have the content required to be picked up plus indexed by the search engines. 4. Challenge the competition A website with good Web Design And Development and one that is effectively developed lets one be on top of their industry as well as challenge the competition so as to keep up. If you keep on working along with adding to the website, this forces the competition to remain behind. When the competition finally realizes the positive effects of a professional website, you will already be established and also making an effort to keep your strong online presence and be on top. 5. Sharing If you see a good website design that is for some business, you may have shared the name of this business and website with your friends and family, just because the website had a good effect on you. The amazing design combined with intuitive site navigation causes a wonderful experience for the user. Sharing causes more traffic, therefore, more potential clients, and this is simply because of the well-designed website. 6. A site compatible with all mobile technologies Having a responsive Web Design And Development is something that is needed. You want your website to look perfect when people open it on a mobile device. You do not want customers to turn away from the fact that your website only looks good on the computer. A responsive design will help you here. 7. Reinforce your brand A quality website has the ability to reinforce your brand. The website should give customers the correct message concerning the kind of business you run as well as why the customer should trust you. 8. Potential downtime can be reduced Poorly built websites contain bugs and also maintenance issues. You do not want a website that experiences problems with the plug-ins, etc. It is important to pursue Website Maintenance so that your site is always perfect. Read Also: Questions To Ask When Working With A Web Developer Best Office Design Trends For 2018 Top 5 Graphic Design Trends For 2017
READ MOREDetails
How to Save Money When Shopping Online
One thing which attracts most of us: discounts, offers, and freebies! Yes? After all, who doesn’t love discounts? And among all, few of the best things about online shopping is the lowest prices, incredible discounts and getting the products delivered at your doorstep without having to make a move. If you also believe that money saved is money earned, this article is for you! We will discuss a few fantastic ways through which you can save money when shopping online. Let’s get started, and we are sure we will give you some real shopping goals (which will help you save money) by the end of this article. Use coupons This is a no-brainer! Using relevant coupons can help you save quite a bit of money, to be frank about it. There are various third-party websites you can fetch coupons from such as TheKrazyCouponLady and RetailMeNot. If you are shopping on Amazon, you can get discount coupons from their coupon section. Compare prices Generally, different websites sell the same products at different prices. Thus, be smart, and use a price comparison website to find the best deals on the same products offered by different retailers both online and in-store. There are various shopping comparison websites you can make use of including Google Shopping and NexTag. Sign up for a newsletter Signing up for a newsletter is another great way of saving money while shopping online. That's so because newsletters are often sent by the retailers to reach out to more people and to attract them towards latest and best offers. When you sign up for a newsletter, you get exclusive access to the recently released discounts, coupons, and offers which will undoubtedly save money. Use a VPN Unfortunately, online stores tend not to price their products the same for everyone. Most online retailers are smart and keep track of your browsing habits by storing cookies on your computer. These files monitor your shopping habits that help retailers in estimating the amount you are willing to spend, and if they see a tendency for excessive spending, the chances are that they will adjust the prices accordingly. Also, a VPN could come in handy when shopping from abroad. Imagine that you're on vacation and you need to order something back to your house in Germany; however, the e-commerce site in question is only accessible from a German IP. With the help of a VPN service, you can easily change your virtual location on a go. Using a VPN in such a way is also a great way to compare prices in different markets as online retailers can show present different prices based on the shoppers geo-location. Read also: 8 VPN Facts – You Should Know About This is often the case when booking a flight. Thus, it is highly recommended to browse and shop anonymously, with the help of a VPN service as it actively masks your IP address and geographical location. Shop at the right time If you are a savvy shopper, you already know that major online retailers keep on changing the prices of items throughout the day. Thus, the same product could be priced differently in the morning and then later in the evening. The way to find the best price is to check the cost of your product several times a day before checking it out. Alternatively, you can also make use of tools like CamelCamelCamel which monitor price changes and issues an alert whenever the price goes down. Further, it is a common trend that prices of the products often go down after a significant event, like Christmas Day, Easter, or Halloween. Check for free shipping A lot of retailers offer free shipping from time to time. However, if your favorite online store is not generous enough, and if you shop online quite often, it is always a good idea to become a member of free shipping websites like FreeShipping.com which provide free shipping for an array of online retailers. Leave items in your cart Have you ever noticed that whenever you leave items in your cart, your retailer attempts to close the deal by sending lucrative emails like ‘your items are selling fast,’ or ‘your items are on discount’? That's so because retailers want you to shop and prevent you from abandoning the shopping cart. Use this to your advantage and leave items in your cart to save money. Earn Cash backs You can also save by earning cashback. Various retailers offer cashback when you shop using specific credit cards, or when you shop for a certain amount of money. Just examine various conditions, and you can easily end up saving a lot of money. Shop at home and pick up in store Shopping at home and picking the item from the store would not only help you in saving shipping charges but also means that you could get a hold of your purchase quicker. Over to You These are a few tried and tested tricks which can come in handy the next time you shop. So, save more to splurge more! Do not forget to share your favorite online shopping trick with is in the comments below! Read Also: The Clever Consumer’s Guide To Shopping Online Ways To Spice Up Your Online Shopping Of Apparels
READ MOREDetails
How to use Video Animation on your Website
Using video animation services is an essential strategy for improving customer engagement and can have a direct impact on increasing the value of your website. It can help you to communicate more effectively than text and so helps your business to communicate more effectively with your target audience. Plus, it marks you as forward-thinking, contemporary, and higher-tech than your competitors. There are several possible uses for animation on your website, from full video to small, functional motion animations. Keep in mind that animation should always be used for a purpose. Visitors have little patience with video content that doesn’t have a point or moving items that slow down navigation and functionality. Product/service animations detail the features and benefits of the product or service in question. Your website already has some kind of text description of your offerings. Add video to connect with potential customers who may not have the patience or inclination to read descriptions, and to add nuance and detail. A good product/service video engages potential customers and gives them a sense of you as a company and what the experience of using your product or service will be like. Explainer videos walk viewers through a process and can be invaluable in helping potential customers really understand and envision how they will engage with your product or service. This raises confidence and makes them more likely to take the next step because they get a more thorough sense of what’s being explained. Explainer videos can also help existing customers operate or troubleshoot a product with greater clarity and confidence. A good explainer video can cut down on service and support calls, and please customers. You can take this one step further by producing teaching videos that become their own product. Storytelling videos take viewers on a journey and create an experience around your brand. These are often used on landing pages, in the “about” section, and in the “team” or “careers” sections. They focus less on a specific product or service and more on who you are as a company or team. They might talk about history, values, locations, or key team members. These tend to be some of the most creative animated and video content on the site and offer a chance to really showcase your brand. One key area to use video on your website is in the career or hiring sections. Using animations to better connect with job seekers gives you an opportunity. You can reach the right candidates by giving a better sense of culture, style, and ethos. There are better ways to make your own animation than ever before. While creating an online video used to require high-powered computers, expensive professional software, and extensive specialist skills, online video tools make it fast, accessible, and simple to create your own animations. Use templates, stock content, and your own creativity to create an effective, professional video for your website on demand. There are many parts of your website that could benefit from animations, and that’s before considering the power of their use on blogs and social media. Start repurposing content into video today to connect more effectively and with a wider range of visitors. Read Also : Information Technology And Business Success: The Things That Connect Them How Does Modern Technology Propel The Success Of Your Business? How To Create An Effective FAQ Page For Your Website Top 5 Graphic Design Trends For 2017
READ MOREDetails
Two SEO Trends to Take Advantage of In 2018
With hundreds of factors affecting Google's search engine results, SEO is no longer a simple science. Gone are the days when you could stuff keywords in an ordinary piece of work and help your site rank high. With ever-changing rules, it is hard to master the art, unless you're working with someone like Scott Keever SEO expert. What you should understand is that the search engines are striving hard to provide their audience with the best search results, and to achieve it, they have eliminated certain ranking factors and introduced some new ones out of nowhere. It means you need to know what has stopped working and what has replaced it. You need to educate yourself about the latest trends, and two of them are mentioned below. The Evolution Of Google Serps Even a few years ago, you wouldn't see more than a few "blue links" after searching. Things have certainly changed recently, and the Google SERPs have evolved lately to the extent that they are quickly grabbing searchers' attention. This, in turn, has helped businesses get more clicks from organic listings. With this latest trend, it is more important than ever to track your rankings in these features and keep a close eye on all those features that appear for your primary keywords. Many SEO tools are now available to help you in this regard. Many tools can help track several SERP features along with their results, which in turn will help you check the features that your keywords have triggered. Another benefit of these tools is that they help you measure the volatility of different SERP features on a regular basis, so you can easily change your strategy. Using Structured Data To Inform Search Engines What it means is that you will have to use structured data in a way that it makes it easier for Google and other search engines to interpret content. It is basically a new and more improved way to format HTML. Interestingly, Google has not confirmed that structured data can affect ranking, but the truth is that you can use it to improve your search listings, especially when you're willing to take advantage of features such as rich snippets and knowledge graph panels. Some statistics show that using the structured data correctly can help improve your CTR by 30% in most cases, and with an increase in clicks, you can see an improvement in your rankings. The fact of the matter is that changing trends in SEO has made it tricky for anyone to rank their business high, but the latest trends show that you should pounce on any opportunity that would help you stand out. That is when you can take advantage of structured data and Google SERPs changing features. If you are still not sure how to proceed, do not take chances and end up making a costly mistake. Instead, let an SEO specialist help you with everything and ensure that you keep getting the juice your website needs to rank high. Read Also : 5 Ways To Improve Mobile SEO Know Why Content Marketing Is Important For SEO How To Monitor The SEO Health Of Your Website
READ MOREDetails
Ways to use Google analytics to find content ideas
Data is one of the most essential aspects which is of high importance to analyze any trend or other matter. For any marketing campaign, the company relies on statistical data massively. The companies which analyze data perfectly and more efficiently are said to understand the customers better. Though data is mostly used to inform SEO, PPC or social campaigns, it can also be used to find better blog content. In today’s world, content marketing is one of the most effective online strategies and small entrepreneurs are working very hard to survive in the business world against giant companies. Thus it is evident that they should come up with new content ideas for betterment. In this article, we will see how Google analytics can be used to come up with better content ideas. Few methods to use Google analytics to find content ideas Find the popular blog types: Try to find the trending blog posts which will provide a way for new ideas for content. The most popular blog posts can be found on the dashboard of Wordpress. This will provide the benefit of knowing what is trending and anyone can plan the blog accordingly. Popular post categories: If you want to know which category of your blog is the most popular, you can know it and thus try writing on those categories for better publicity and success. Though Google Analytics does not allow you to see directly which blog categories are most viewed by default, it can be done. To do this, you need to enable custom dimension tracking on your site. This will make you see which categories of your posts are most viewed and liked. Most searched keywords: You should have high-quality content to rank well or your posts will be lost down due to changing search algorithms. It is easy to come up with some content ideas by gathering some low hanging SEO fruits. If there is any search bar on the site, you can easily look for the keywords which people search for when they look for your blogs. This will help you to write your content accordingly keeping in mind what the public is demanding, and this will bring you immense success. To do the task in Google Analytics, go to behavior > site search > Search terms to finally locate these keywords and you can plan your content accordingly. By knowing the keywords you can plan your topic and know the lags that you were having in your content before. The search term reports will also give you the idea about what the viewers are looking for and you can choose the idea of the content depending on that. Intent of keywords: Google wants to serve its users in every possible way. It provides value to its visitors and thus provides various options. If the keywords given in your post are matched by the need and intent of the users, then it will make your post more useful and will increase the rank of your page as people will start liking your post more and this will bring you success in the field. There are basically four types of keyword intent that anyone should be aware of: Navigational, Informational, Investigational Transactional. These types of keyword intent can help anyone to write posts and fix their keywords accordingly to attract more users and more readers and establish the content widely. To discover the intent of the users visiting your site, you can look for your search queries report by going to Acquisition > search console > queries. Thus it can be said that you should focus on the keywords so it can match the intent of the users and your posts can be viewed by many users. You should stick on the keyword intent type following your category and content. So, for a better result, focus on the right set of keywords and see your posts getting viewed massively and see the number of views in your posts increasing day by day. This step is very helpful for coming up with content ideas and succeeding in the field of content marketing. Advanced segment: Another most productive way to get writing ideas with the help of Google analytics is that a special question advanced segment can be created and this segment can be used to identify the question and answers of the customers. The procedure is given below: Click on advanced segment > click new custom segment> click to box next to include> find and enter keywords which will indicate a question > click “add or statement” and add another keyword that would indicate a question. This can also be helpful to get writing ideas and this will benefit any content page to succeed and establish itself remaining ahead of the others. To know about other various advantages of Google analytics which can help us to come up with various ideas can be found on the internet or contact SEO company. Google Analytics is very useful for performing various online operations and is a friend on whom we can rely on. These ideas can prove to be very helpful for the small business organizations as it may give them ideas for better contents to fight against the well-established and powerful organizations. To rank higher than others, the content should be well written and of high quality to come into consideration by the viewers and to increase the popularity of your posts. For any content management team, it is very important to take care of the keywords and the most typed words. If the keywords of the topics are matched with the searched words of the users, then there is a high chance that your post may be shown at the top rows and there is a chance that your blog will be viewed. These points will help you with ideas to write better contents with the help of Google Analytics and will bring your webpage more success and acknowledgment. Read Also : The 10 WordPress Plugins Every Successful Blogger Uses Avoid These 5 Mistakes Before Starting An SEO Oh, Crop! Killer E-Commerce Mistakes You Need To Conquer
READ MOREDetails
Different Ways to backup your hard drive explained
If you have not been backing up your data, you are not playing safe. It is a practice that you should make a habit of. Why? There is a high risk for you to lose your data when your hard disk drive fails when your computer is stolen when a disaster strikes, or when malware infects your computer. It is imperative for you to safeguard yourself from these incidents, and the only effective way to achieve this is by backing up your hard drive. Besides, backup methods save you time and money, and they could give you a competitive advantage. Additionally, some data is irreplaceable and losing it would be a disaster. That’s why this article will explain some of the ways to back up your hard drive. Local drive : One of the best and most efficient ways to back up your data is by transferring all your data to a local drive – one that is separate from your computer. Backing up on another hard drive is an easy and quick process, especially if you have several drives attached to the system. You could back up your databases and files to an external drive, a USB flash drive, or even a secondary drive. Moreover, you could save your hard drive data to a different drive on a computer that is connected to your network. Keep in mind that the backup process when using a local drive varies. You have to ensure to carry out the backup steps appropriately. It could save you a lot of trouble when your data gets lost. Cloud storage : Another effective way to back up your hard drive is by relying on cloud storage services. In recent times, this backup method has become one of the most revered. Its popularity has risen because it can be done automatically, and you get a particular amount of storage space for free. Moreover, you could access your files and data from any location so long as you have a good internet connection. There are some cloud storage services, and you should choose the one that works best with the size of your data and files. You can test these services for yourself by logging on to ottomatik.io, which is one of the best cloud storage services. Other reputable cloud storage services include OneDrive, Google Drive, Box, and Dropbox. Some of these storage options are free, some require you to pay, while others are free but with paid extras. Drive cloning : Well, if you have considered other backup options and you are still not content, you might want to consider drive cloning. It is another effective backup option; albeit not as popular as the methods above. So, what exactly does it entail? It works through a clone hard drive, which is a second drive that has an exact mirror image of your original hard drive. Unlike in the earlier days when drive cloning was an expensive strategy, storage management companies have come up with excellent software, making the process more seamless. Using the software available, you can create an exact image of your hard drive fast add efficiently. 3-2-1 strategy : The whole idea behind backing up data and files is to ensure that all vital information is fully protected. That is why you should consider a 3-2-1 backup strategy. It is a strategy that requires you to rely on multiple backup options. When you choose this strategy, you should ensure to create three copies of your hard drive data to avoid losing it. You should also ensure that you store one copy of the data you’ve backed up off-site. This ensures that your data is safe from natural disasters and theft. Also, you need to utilize two data formats. With this strategy in place, you will hardly lose any data. Conclusion : There are numerous backup options, and all are meant to protect your hard drive from total data loss when a natural disaster strikes or your computer crashes. Backing up your data helps you save a lot of time, effort, and money that you would spend trying to recover lost data. You might want to consider one or all of the methods mentioned in this article. They could save you a lot of trouble. Read Also : 5 Indispensable Things To Keep In Mind While Picking A Hard Drive How To Securely Wipe Your Confidential Data From A Hard Drive 5 Actionable Mobile Marketing Tips That Drive Sales
READ MOREDetails















