Are you an android user? Android seems to be one of the secure phone operating systems. But do you know even though the android has lots of security features the hacking is possible? Yes, the any-third party can easily enter your system and hack your phone data.
Hence when you know how to fix a hacked Android phone, you do not have to take any messes regarding the third-party interventions on your private space.
Let’s see the process of how to fix a hacked Android phone and block the third-party intervention. But before all, you have to know how you will know that your phone has been hacked? Then, when you are using the android phone, you will know that your phone has been hacked within a few security checks.
How Do You Know That Your Phone Is Being Hacked?

Android is one of the safest phone operating systems. Hacking android phone recovery is possible when you know that your phone has been hacked. And you can take further steps on how to fix the hacked android phone.
When hackers are breaking into your system, the hackers have to install any malware in your android device to keep tracking your phone activities. The malware functions are going to interrupt your device’s regular activities.
Here are some signs which are going to tell you that your phone is being hacked. And this is the first checking point before starting the process of how to fix a hacked Android phone.
- Poor phone speed and performance.
- Your phone is facing low signal strength.
- Phone apps are frequently crashing, and unknown apps are installed.
- Spam pop-ups.
- Sudden Increasing data usage.
- Changes in call settings in your android device are clear indications of hacking.
If you are identifying these sudden changes in your phone, you can clearly say your phone has been hacked. After facing these problems, the android phone users are asking how my phone was hacked. How do I fix it? Here we are discussing the easiest four solutions for this problem.
How To Fix A Hacked Android Phone?
When you want to know how to fix a hacked Android phone, you have to start by identifying the problems. Then when you identify the problems, you can begin the process of how to unhack your phone. Before starting, take all the backups of your phone.
Here are the solutions for the android device administrator hack.
1. Clear The Cache Memory
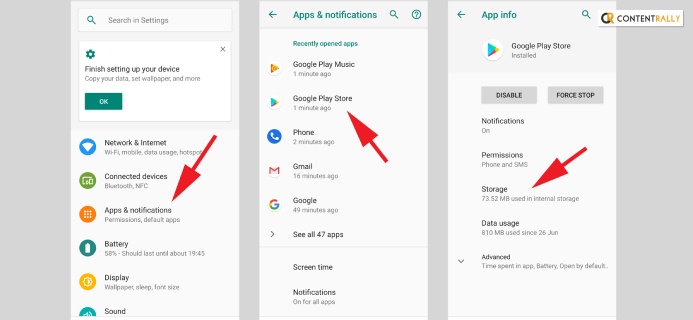
Clearing the cache memory is the first trial step for how to fix a hacked Android phone. When malware is installed in your system, your cache memory carries the sign of the installation. So first, open your android device in recovery mode.
Then wipe out the cache portion of the memory. Choose the phone cache memory, then the device cache memory, and wipe out the whole cache memory from your device. Then restart your device again.
2. Run The Antivirus Scan And Delete The Suspicious App
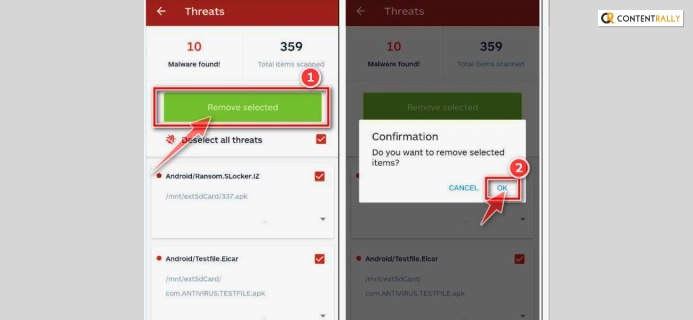
Android phone mobile antivirus systems are relatively stronger. First, when facing the low-speed problem, first look into the system’s other apps and run your antivirus scanning. The best way to block hackers is to keep your system updated and always scan your device. When you are stopping the auto-updating options, there is a chance of third-party interventions.
First, open the Android settings. Then check all the apps. And if you are going to identify any apps which you can not remember to install. Then, identify and start the process of uninstalling it; after uninstalling the app restart your device once.
3. Disable Call Redirections
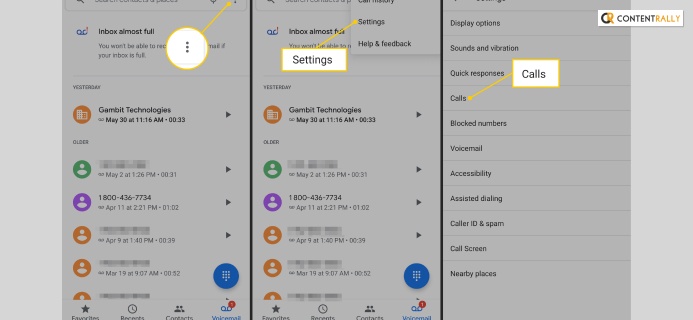
This is another step of how to fix a hacked Android phone and find the hacker. When you are redirecting your calls to another number, the malware is going to track your activity. And after you are diverting any calls to the other number, the hacker will also do the same process.
The hacker starts getting the other device’s information to their devices. After that, you can simply dial the USSD code from your device to know who is getting the information on the devices. This step is not only to fix your problem; you can find out who the hacker is.
4. Factory Reset And Delete All The Data
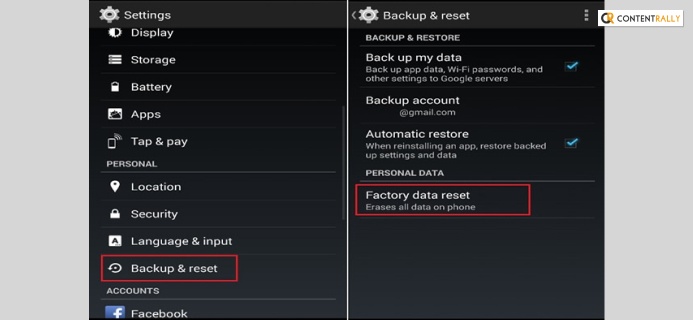
Factory resetting is the ultimate step you can take to fix the hacking problem. But before starting the factory resetting, it is better to take all the backups from your devices. Because after the factory reset, you will face a data loss problem, all of your data of the messages and contents and other information are going to be deleted.
Every android phone has a factory reset option. Follow the following steps and delete all existing data from your devices.
Step 1: First, start with opening the android phone settings options.
Step 2: Then tap on the search icon of the settings option and type the factory reset command there. Press enter to run the command.
Step 3: Open the resetting option and click on the erase all data options from there.
When you are going to delete all the data from the devices and the malware, every other essential data will also be erased. So before doing the factory reset, always take the backups of the data. After doing the factory reset, your android phone is functioning as a new one.
5. Enable Two Factor Authentication
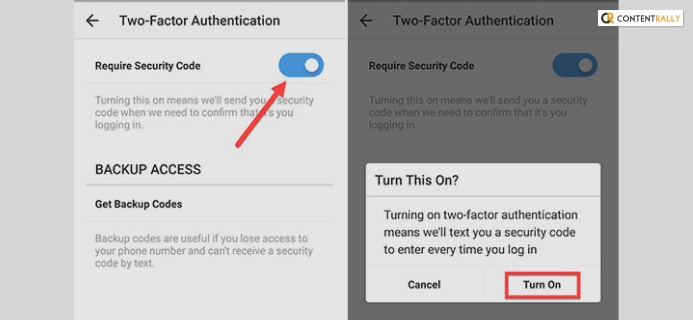
Nowadays, there are many sites that offer two-factor authentication, and it can safeguard your android phone with ease. It can make your device safe and secure from the clutches of hackers. It is one of the best options to fix it within a shorter time frame.
6. Enable Biometric Authentication
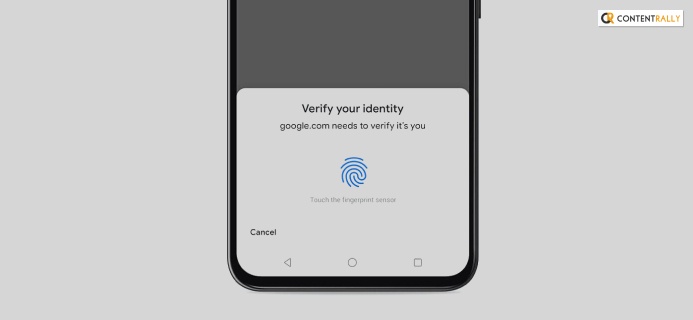
Biometric authentication is one of the best ways to protect your phone from the clutches of hackers. It can make the life of hackers difficult if you enable biometric protection in your smartphone.
Sometimes, the inbuilt security will enable your phone to offer biometric authentication and will enable you to keep your smartphone safer.
7. Never Register On A Vulnerable Website

You must not register through a vulnerable website that can tamper with the information present on your android phone. It can help you to achieve your objectives in an effective manner.
8. Change The Passwords Of Your Online Accounts

If you think that your phone has been hacked, then you must ensure that all your online account passwords and user ids are changed. It can make your device less vulnerable to hackers within a shorter span of time.
How To Protect Your Android Phone From Hackers?
You can follow certain simple steps to protect your android phone from hackers. Some of these steps are as follows:-
- Make use of the Pin or the password in the lock screen.
- Lock all the required apps on your device.
- Try to download the apps from trusted sources.
- Read through the app permissions before you download any app.
- Download the device manager for android.
- The application of the Google authenticator is a must-have feature to consider.
Frequently Asked Questions (FAQs):
Some of the common symptoms of a hacked Android Phone are as follows:-
1. You will find a random unwanted app install going on on your phone.
2. Within a few seconds, you will experience poor battery life or extreme battery usage.
3. You can view the weird pop-ups and ads.
4. Unusual as well as high data usage.
5. Your phone and apps will keep on crashing.
With the help of the factory reset option, the majority of the malware can be removed from your phone. It can help your phone to stay away from the clutches of hackers. However, it can remove the photos, images, notes, and contact details from your device.
If your phone is hacked, then you can clean your phone with the help of the factory reset option. It can fix your phone from the chances of damage within a shorter span of time.
Yes! The hacker can see through your phone camera once he gets access to your phone. You have to stay vigilant in this regard to make use of these systems to make things work well in your way.
This code you can use to check whether your phone is being tapped False by the hacker or not. You have to identify these facts while using a hacked phone.
Wrapping It Up!
These are the most accessible four solutions of how to fix a hacked Android phone. Among these solutions, only the cache memory is clear, and the factory reset options are causing a data loss problem.
If you currently do not want to face these problems, try simple solutions like reboot your system and the virus scanning.
Hence, if the problem is not resolving, try the cache memory clear and the factory reset options. But recovery is possible within a few minutes. So what is your android using experiences? Do not forget to share your comments in the comment sections.






















