Overview of Recovering the Memory Card/SD Card:
If you are facing a problem of unexpected loss of data from your Memory Card or SD Card and your important and loving pics deleted. This type of bad things always will occur when you go outside with your family or with your friends and take some pictures on a memorable trip with your Phone or Digital camera.
But you don’t transfer all these precious pictures to your computer, one of your family members or friend accidentally deleted your photos or formatted your SD card/Memory card and there is no backup of all these photos.
If you are facing the same problem that is explained above so you still have a chance to get back your deleted photos from EaseUS SD card recovery software.
Download Free SD Card Recovery Software:
Usually, SD card is used in mobile, digital cameras, cell phones, music players, video games, digital cameras and in other electronic devices for the purpose of data saving. But sometimes data will be lost from your SD card due to the reason of accidentally deleted or formatting. For this free data recovery software helps you to recover data that is EaseUS Data recovery software is available to recover your data.
It is the perfect SD card recovery software and worked well for your deleted data. This software will help you to recover deleted or lost pictures from your memory card in all situations. The EaseUS SD card recovery software supports different brands like Samsung, Integral, SanDisk, Kingston, PNY, Panasonic, Lexar, Verbatim, Sony, Fujifilm, etc. in simple steps.
How To Recover All Deleted Files From SD Card Complete Guide:
Now in this article, I will show you how to use this easy, simple, new modern interface free Data recovery software to get back your deleted data into your SD card step by step. This guide can also be used to recover your deleted files from your external hard disks like USB drive and many other storage devices.
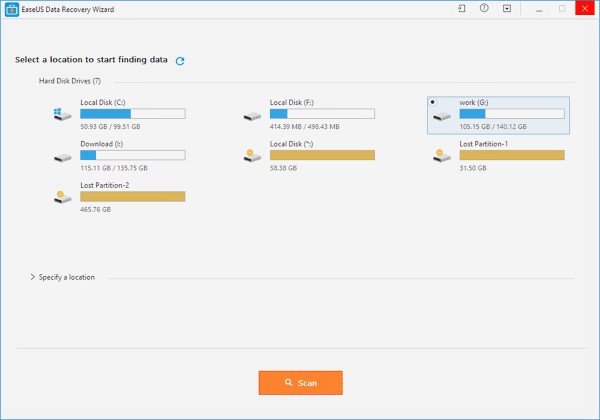
Step 1: First you have to download the free EaseUS Data recovery software into your computer or Laptop and after this connect your SD card to your computer and launch the EaseUS SD card recovery software. Now select the card option and then click on the scan button to scan the SD card.
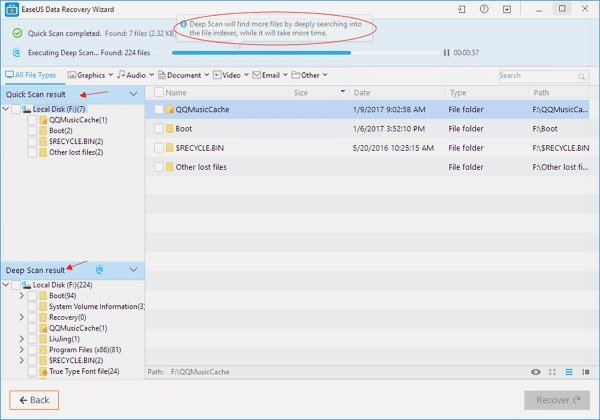
Step 2: Now the EaseUS data recovery software will start first simple scan will start to recover your deleted data on the memory card. After this, a deep scan will start automatically to find the more deleted files from your memory card.
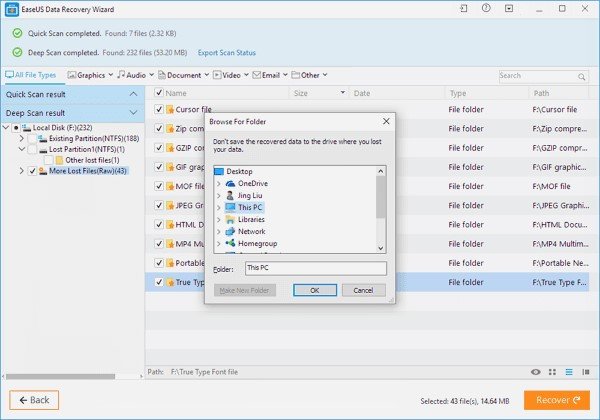
Step 3: After the fully scanned the EaseUS SD card recovery software will give you permission to see some files like photos, documents, and many more files. And you have to select all those files that you want back. After all this process you have to click on the recover button to get back all your selected files. Now you should save all your recovered files into another device.
Conclusion:
EaseUS data recovery software is free software and you can download it free and try this software to get back your deleted files due to accidental deletion or virus attack or any other reasons.
Read Also :