If you’re the regular user of Mac, then you may already be experiencing that your Mac slows down if there are no cleanups time to time. Here is the quick guide to clean up your Mac without any problems.
Delete the Large Unused Apps :
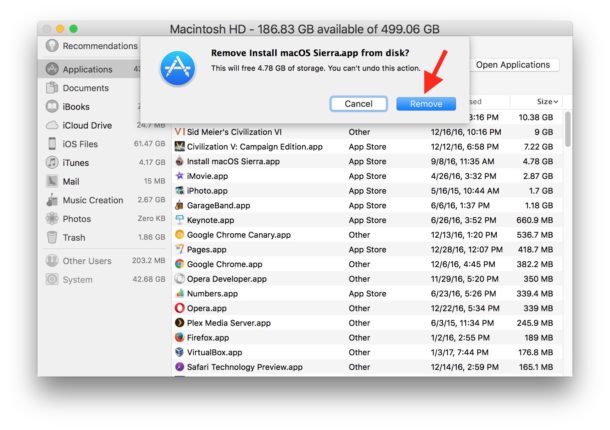
Many users have unused applications that are big and occupy the ample space on your Mac. With the view to clean up the Mac, make a note that you need the macOS Sierra or later version to have the cleaning characteristic operating. The earlier version lacks the storage control device. Make certain that you have taken the entire backup earlier than deleting the apps. Take the following steps for cleaning up the large unused apps.
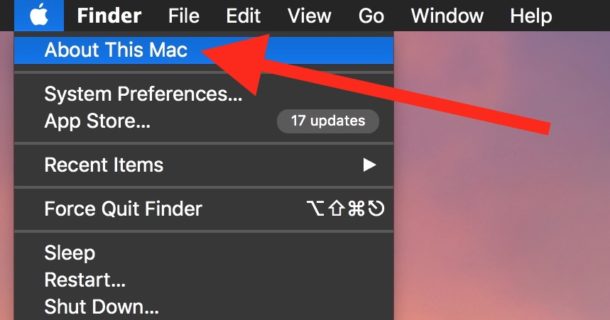
1. Go to the Apple menu, choose the ‘About this Mac’.
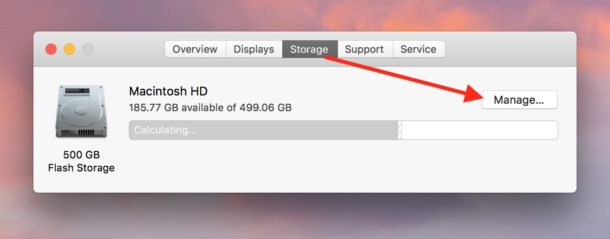
2. Select the Storage option on the window that prompts up and clicks the Manage.
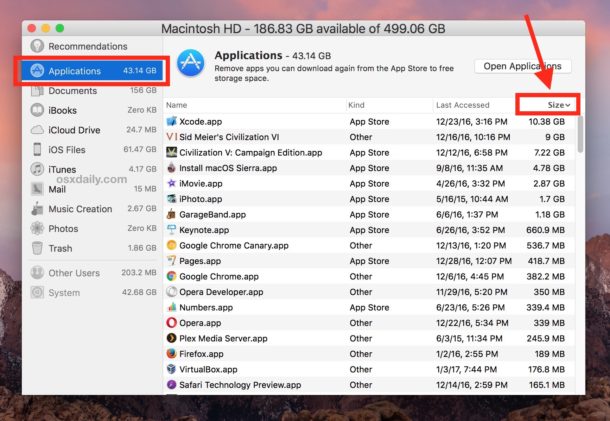
3. Select the application that is available on the corner of the screen to the left.
4. Choose the size menu and click to the drop down to have the list of apps from largest to smallest.
 5. You can also check the last access to the apps.
5. You can also check the last access to the apps.
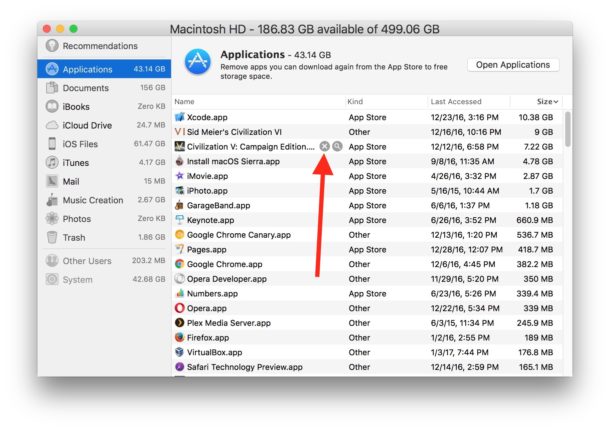
6. Locate the list of apps that you no longer need and delete them by clicking
‘X’ button.
 7. Select the ‘Remove’ button in the prompting window.
7. Select the ‘Remove’ button in the prompting window.
 Clean the Cache :
Clean the Cache :
The top reason for slowing down your Mac is the cache that accumulates over the passage of time. Caches are the temporary files that enhance the speed of the data when reloaded again. These caches can be app cache, library cache, browser cache, system cache and plenty of more. For in-depth details on cleaning up your Mac, you can visit this page. Actually deleting them won’t solve your problem as there is the leftover which develops over the period of time. Follow the under-noted method to absolutely clean the cache.
- Select the Finder logo from the dock.
- Click the Go menu which can be found in the upper corner to the left.
- Select ‘Go to Folder’
- Get the list of caches by typing ~/Library/Caches
- Lastly, right-click the folder and sent it to the trash and then empty it.
Uninstall Unused Applications :
This is one of the essential steps in cleaning up the Mac. The primary area that is consumed on the Mac is through applications. You need to delete at least the unused apps from the Mac. If you think that by sending those to trash can delete the app then you’re truly incorrect and as there are several leftovers by the app that occupies the space in the memory. In order to clean them absolutely, you must navigate through the beneath folders and trash them.
- App preferences are located in ~/Library/Preferences/
- Support Caches can be found in /Library/Caches/ and ~/Library/Caches
- App states are found in ~/Library/Saved Application State/
- Application files are found in ~/Library/Caches.
- Binary and dock icons are found in /Applications/
- Crashes are located in ~/Library/Application Support/CrashReporter/
- Plugins can be found in ~/Library/Address Book Plug-Ins/
- The library can be located in ~/Library/
Remove Apps Consuming More Power :
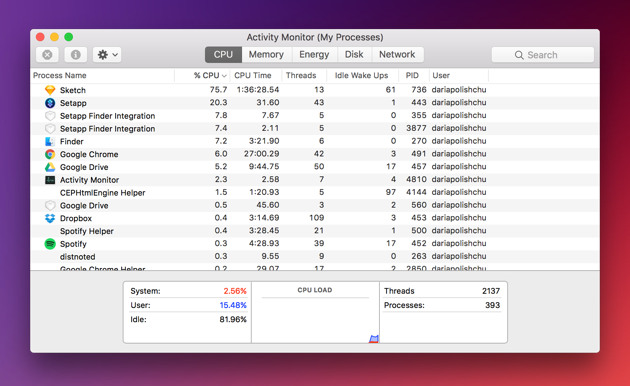
There are some apps that eat up the extra power while running. You should use the activity monitor to see the apps that are consuming more power. In fact, you will easily see the five specific details including CPU, Memory, Energy, Disk, and Network. For the Mac to run the problem-free, you have to select the ‘-‘ button and clear away the apps that you think is occupying extra power and they are unused too.
Delete the Large Files :
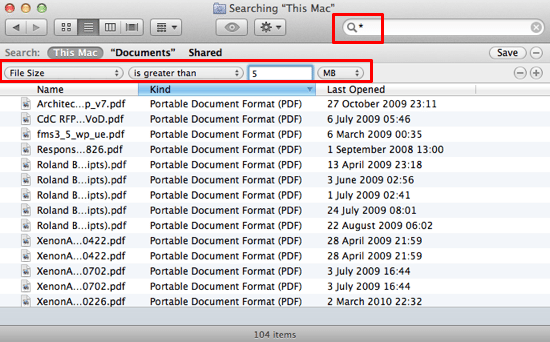
This is one of the crucial ways of cleaning up the Mac. You can carry out this effortlessly and quick by using Finder. Open the new window within the Finder. You may be able to see the search box in the top right corner of the display screen. Press asterisk inside the search box. Add the “+” which you will be able to see below the search box. Apply two filters in that window. First one for the size and the second one for the ‘is greater than’. Enter the size say 30 GB. You could also choose the alternative column for GB or MB. Whilst you apply those filters, you will able to see the effects matching your criteria.
These are the essential ways that help you to clean up the Mac without any problems. Follow them and you can have the best performing Mac.
Read Also :