Most organizations use at least some form of cloud storage, yet security issues are still a top concern. Data loss and security breaches are always in the news, with some of the most high profile data breaches to happen in 2018 so far including those that occurred at Reddit, Timehop, and FedEx.
What this shows us is that even large companies can make mistakes that seriously compromise the security of their data.
A 2017 survey conducted by Clutch revealed that while confidence in cloud storage security is high among small businesses, most are not doing enough themselves to protect their cloud storage. After all, cloud security requires involvement from the user, as well as the provider.
We go over some of the top cloud security controls your business should be using to help ensure your data is adequately protected.
Why do you need cloud security control?
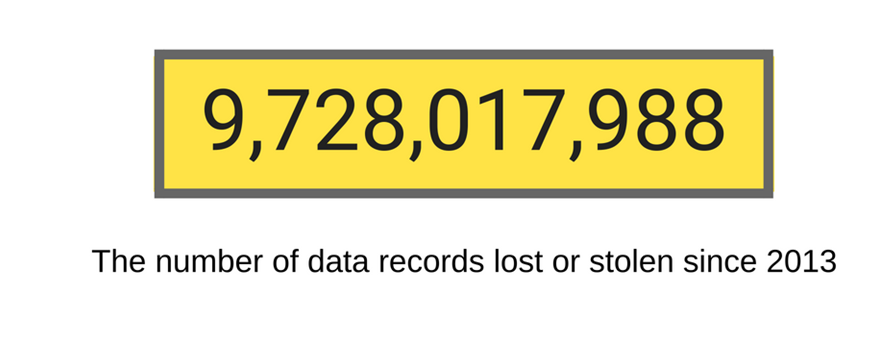
Every day, sensitive information continues to fall into the wrong hands.
That’s according to Breach Level Index, as of August 2018.
While cloud computing can be great for businesses, providing several benefits such as cost savings and data portability, it does come with certain information security risks. To protect your business against vulnerabilities, you need to put specific controls and standards into place.
That’s where cloud security controls come in.
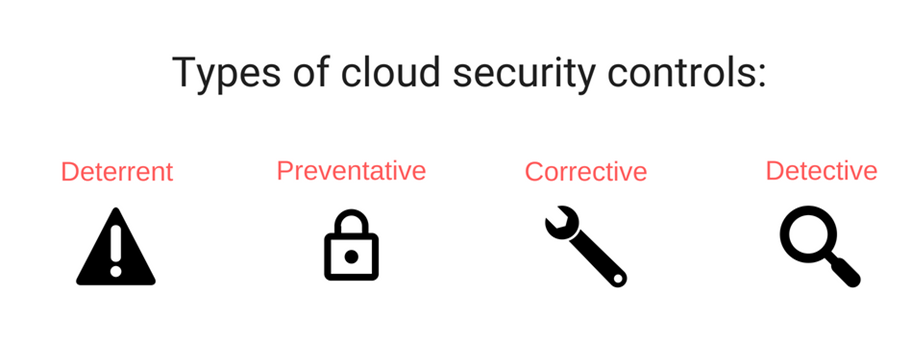
They help to address, evaluate, and implement cloud security. They can include the following types of controls.
- Deterrent: These serve as a warning to potential attackers, warning of possible adverse effects if they were to proceed in their attempt, thereby helping to deter unlawful access.
- Preventative: These controls strengthen the system against attacks, protecting and managing vulnerable parts of the storage.
- Corrective: These help to reduce the consequences of an attack, which typically involves limiting damage. This could take place during or after the incident occurs.
- Detective: These controls will identify or detect an attack, and then respond to the incident. If an attack is detected, the detective control will signal to the corrective and preventative controls in an attempt to minimize damage.
Using different types of controls will help to limit and prevent potential damage when using cloud storage solutions.
What seems to be the problem?
What businesses need to understand is that you cannot rely on your provider to do all the hard work. The issue is not that the cloud environment itself is insecure, but that customers are failing to configure their networks, applications, and data accurately.
For instance, let’s take a look at what went wrong with Timehop. On 7 July 2018, the company was affected by a significant data breach that included email addresses, names, dates of birth, and phone numbers being taken.
What was the issue? A cloud account that didn’t have multi-factor authentication.
For Reddit, although they had two-factor authentication in place, their SMS-based authentication was not as secure as it needed to be.
As for FedEx, the problem traces back to Bongo International LLC, a company bought by FedEx back in 2014, which had been storing sensitive client data on an open Amazon S3 bucket. The data had been available for public access for several years, having been collected from 2009 to 2012.
Data can be put at risk in many different ways, so it’s essential to have the proper controls in place from the start.
Find out what you are responsible for
Many cloud services will offer some level of security. What companies need to do is find out exactly what they are responsible for when it comes to securing the data that is uploaded to the cloud.
Ignorance is no excuse. Speak to your provider and find out which cloud security controls you are responsible for and what services they offer. Whatever tools are at your availability, make sure you use them all.
Ultimately, you are responsible for securing your data, so take advantage of any security tools at your disposal, then make sure you take care of the rest.
Limit cloud access
A good way to reduce risk is to limit who has access to the sensitive information you are storing. Public cloud storage resources, such as Amazon’s S3 bucket, should not allow external access. Leaving SSH open is another common mistake.
You should only allow those who must use the data directly to carry out their job to have access to the data. You can grant temporary access on an as-needed basis to any additional employees.
Make the most of the identity and access control tools used by most major cloud providers, so you always know who has access to your data.
When granting access, you have the option to limit what data someone has permission to access. Delegate appropriate permissions as needed and remove or disable accounts if an employee leaves the company.
Keep your data secure
One of the most common mistakes that companies make is to leave data unencrypted. You want to be sure that even if all other security measures fail, you have at least encrypted your data as a last measure of protection.
While some providers offer encryption, companies should still use their own encryption techniques alongside these. Your decryption keys should remain within the company so that you can maintain control over these at all times.
Learn from past mistakes
Even large companies make mistakes when it comes to cloud security.
You cannot merely rely on your provider to handle all aspects of security. Users need to ensure they are using current cloud security controls to ensure their data remains secure.
The good thing is that we can learn from others’ mistakes.
You can take extra precautions and implement certain controls and standards to improve security. Just make sure you pay attention to what is happening in the world of cloud security and update standards and controls accordingly.
Read Also :