When it comes to protection, you can choose very few select products for your Mac device. The reason is that there are only a few antivirus companies that have the configuration and programming best suited for protecting Mac computers. However, all companies will claim to provide all-around protection to your Mac notebook. The main question is how you can actually tell which one to trust. Bitdefender Antivirus for Mac is one of the best and most reliable antivirus programs that you can find.
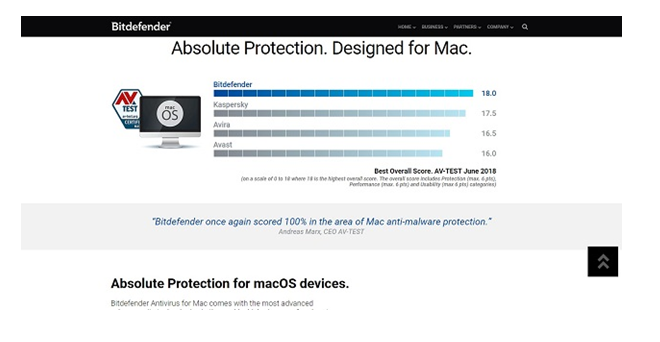
According to Andrea Marx who is CEO of AV-TEST, Bitdefender scores 100% in the arena of antimalware protection on all the Mac devices.
Perfect protection for your Mac :
Bitdefender promises to provide you with the best experience regarding both cybersecurity technology and affordability. It claims to give you the fully-fledged freedom to use Mac devices at their best.
The latest update of Mac assures you against all the threats that are both common and rare to the Mac device. Bitdefender, with its multiple layers of protection, will prolong the longevity of your device. It is equipped with multilayer protection against all types of ransomware. Added to that, Bitdefender will provide you with a shield against any and all online threats. Using Bitdefender will drastically improve all of your online experiences.
Often you have been plagued by advertisements that suddenly pop up while you are watching a video or playing some online games. Installing Bitdefender will prevent those advertisements to pop up and it will block them. It will grant you seamless viewing experience. It will also ensure that the performance and speed of your Mac improve drastically.
But the best part is that Bitdefender is one of the few antiviruses that incorporate the goodness of cloud-based technology. Bitdefender will provide you with a constant guard against all the malicious attacks by cloud-based technology 24/7. Like much other mainstream antivirus software, Bitdefender offers a thirty-day free trial for all their products.
Features Of Bitdefender Antivirus :
Take a look at the specifications and functionalities that Bitdefender offers you:
Bitdefender Shield:
A specialty of Bitdefender is the Shield protection that is provided with it. From smaller threats to complex threats, Bitdefender will handle all the nitty-gritty of your security needs. The software is equipped with unique proprietary technologies that will automatically detect and eliminate all kinds of threats. All you need to do is to turn on the Bitdefender Shield and sit back.
Time Machine Protection:
One of the specialized features of Bitdefender Antivirus for Mac is Time Machine Protection. The feature that will automatically back up all your files saved in your Macbook and will provide protection from all types of ransomware attacks. This will also be extremely useful against ransomware that tries to encrypt and destroy all your personal and confidential data.
Safe Files:
TheSafe Files feature is a feature that will allow you to save all your files in a special folder. Keeping in this folder will ensure that your data will be protected from any kind of unauthorized changes. All you need to do is to add all the folders into its watch list. The applications that you will trust will only be allowed to access all these files that have been added to the watch list of the Safe Files feature.
Blocking and removal of ads:
No one likes spontaneous advertisements flying up in their programs. Even Macs can get nosy adware contaminations that redirect your browser and drive you up the wall. Bitdefender identifies and eliminates adware, noxious criminal projects, annoying toolbars, and other irritating program additional items so that you can make the most of your Mac.
Super-Fast Scanning:
Ironclad insurance is an extraordinary thing, yet it’s far superior when it accompanies unrivaled speed and execution. Bitdefender consolidates exactness and speed, so you get ultra-quick outputs and the best identification rate in the business.
Autopilot Feature:
The new Autopilot has been designed as a Security Advisor and its purpose is to give you a more streamlined experience with your security. Its shrewd abilities imply that it can carry out security activities without hogging resources or bothering you with endless requests and notifications.
Cloud-based security:
The continual updates ensure that all your system remains protected by Bitdefender at the highest level of protection. However, viruses and ransomware get updated continuously too. In fact, the updates are designed only after the newer threats emerge. The latest threat that has emerged is in the form of cloud computing attacks. Bitdefender Cloud-based security advances to distinguish and take out e-dangers, wherever they may originate from, to give you continuous overall insurance. As the hard work is done in the Cloud, there’s no delay in your Mac’s performance, and your own data remains secure on your PC.
Anti-Phishing features:
With the rise of online transactions and more and more reliability on online banking, the threats to the online bank data and piracy are on the rise. Online scams are an especially dangerous thing that can liquidate all your life’s savings within seconds. The anti-phishing technology from Bitdefender will help you to keep your device and personal banking information safe and secure from all the phishing attacks. It will automatically detect and block all the websites that mask as trustworthy banking sites. It will adeptly protect all your data like credit card details, passwords, net banking information, customer id, etc.
Final Verdict :
Seeing all the advanced features, the verdict is to go for this antivirus without any second thoughts. Tried and tested by all the experts all around the world, Bitdefender is the best antivirus that will serve the protection of your Mac device very well. All you need to do is to install and subscribe via the available online subscription. There is very little difference between the home use antivirus and commercial use antivirus. So go for it!
Read Also :