On May 21, 2020, Pac-Man Doodle completed by 40 years. It was launched in the early 1980s. It was the most famous arcade game till now.
As I know, Pac-Man was a massive hit in pop culture. It is still strong today. But the interesting fact is Pac-Man is made with full certainty.
The designer Toru Iwatani initially had no interest in games. But his creation got the success that surprised him too. Here are some exciting facts behind the scenes about Pac Man’s making. So, keep on reading till the end of the article.
Google Pac Man Doodle: Interesting Facts
Pac Man is a Japanese video game created by Toru Iwanti in the 1980s. He is known as the father of Pac Man. But it is developed, published, and owned by Bandai Namco Entertainment.
Google Doodle celebrated the 30th anniversary of Pac-Man on May 21, 2010. After this celebration, Google PacMan Doodle gained a mass audience. Many people got to know about this classic arcade game due to Google. Now it is also available on Google Play.
This huge popularity of arcade games has many hidden facts that can be an influential matter. Scroll down to get the fascinating facts.
Read More: How To Delete A Page In Google Docs
1. Toru Iwatani, Pac Man Designer Had No Training

Toru Iwatani started work at the age of 22-year-old at Namco in 1977. But he has no particular interest in making video games.
Before Pac-Man, Iwatani was busy to designing Cutie Q (1979), Gee Bee (1978), and Bomb Bee (1979), but before ended up these games, two years later, in 1980, he launched Pac-Man.
2. Pac Man Inspired By Space Invaders

The theme of the Pac-Man Doodle has come from the success of Space Invaders and Galaxian. Pac-Man Doodle was a masculine space, full of dark shooting space, which was popular among the people.
In 1986, Iwatani said, “All the computer games available at the time were of the violent type—war games and Space Invader types, there are no games that everyone could enjoy, and especially none for women. I wanted to come up with a ‘comical’ game women could enjoy.”
This is the reason the father of Pac Man isn’t copied from war games. Instead, he takes the theme of black but not violence. Iwatani began to think about making the game ‘comical’. He takes the idea from the word ‘taberu’, which means ‘to eat’. And eventually, the concept of the game is called ‘Pakku-Man’.
3. Pac-Man Doodle Shaped Inspired By Pizza
Do you know how Iwatani got the idea of the shape of Pac-Man? While he was eating a pizza, it looked like a pie missing a slice and it had become the shape of Pac Man Doodle. How interesting it is!
In an interview, Iwatani exclaimed that “In Japanese, the character for mouth [kuchi] is a square shape. It’s not circular like the Pizza, but I decided to round it out.” And thus, Pac-Man was born.
4. Pac Man’s Ghosts Were Motivated By Comic Book Characters

As Iwatani began to develop the idea, he added the concept of the maze (a power cookie), which has the extra power to eat ghosts.
Later, the creator revealed that the power up idea had come from Popeye, who defeated his arch-rival Bluto by eating spinach.
Now you may want to know where Iwatani gets the idea of ghosts. It’s another interesting fact of the Pac Man doodle. He said that he takes ideas from comic books. When he was a kid, he watched animation and manga. For instance: Casper, Obake no Q-Taro.
5. Pac Man Was The First Game To Introduce Cut-Scenes
Pac Man doodle is a very simple game. It is a cartoon-like interface, where you can see an enormous Pac-Man chasing a terrified ghost across the game screen.
But, Iwatani’s programmers wanted to implement the idea from “coffee breaks” and argued that interludes a little bit to the game, but the father of Pac man won this battle.
6. Pac Man Is Nothing Without Enemy AI
The behaviors of the ghosts were the most tricky part while Pac Man was programming, Iwatani stated. He also said that it takes 18 months to develop the games. His sound designer Toshio Kai, and Programmer Shigeo Funaki failed to create something more entertaining.
Iwatani admitted,
” There’s not much entertainment in a game of eating, so we decided to create enemies to inject a little excitement and tension.”
One of the most intelligent aspects of Pac-Man Doodle is that each ghost behaves differently. If you play Pac-Man doodle, you can see one ghost chase the player while trying to attack Pac-Man from the front; the fourth will chase and suddenly change course.
Iwatani said that,
“This is the heart of the game … The AI in this game impresses me to this day!”
7. It Was Unexpected To Be A Hit

At the beginning stage of the arcade game Pac Man was not thought to become one of the most popular games among the masses.
Iwatani exclaimed in an interview that the game might be popular among youngsters and women. But, American Distributors picked up “Puck- Man” and named it “Pac -Man” and the rest is history.
8. Pac Man The Most Successful Arcade Game

After launching this game in the early 1980s, within 18 months, 350,000 arcade machines were selling and generating more revenue. But Iwatani, the father of Pac-Man, the designers and programmers, was working in Japan at the time with Tomohiro Nishikado, the creators of Space Invaders did not directly profit from all the success.
In 1987, Nishikado said, “The truth of the matter is, there were no rewards per se for the success of Pac-Man, I was just an employee. There was no change in my salary, no bonus, no official citation of any kind.“
You May Like To Read This: Pros and Cons on Google Translation Accuracy
9. You Can Make The Highest Score Of 3,333,360 Points
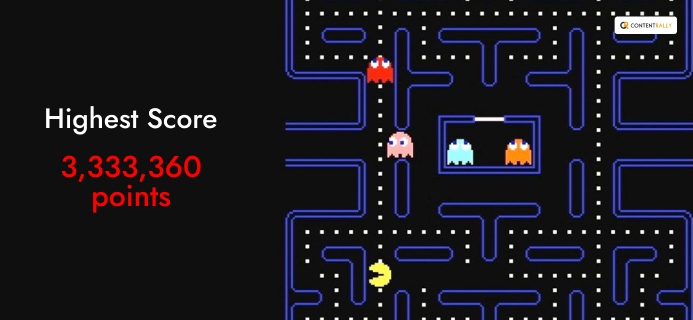
Pac- man does not have a so-called ending as such. But, if you consumed every dot, fruit, and power pellet on each of the 255 levels, you can get a maximum score of 3,333,360 points.
Legendary video game champion Billy Mitchell was the first one who won this maximum Pac-Man score.
10. Google Doodle Pac Man Still Be Played Today

Google celebrates Pac Man’s 30th birthday and launched Pac-Man google doodle of the playable version.
According to the report issued by a time management company, the game takes 4.8 million working hours. This is the first-ever Google doodle that can still be played today.
Frequently Asked Questions (FAQs):
Here is some more information regarding Pac Man doodle, you can look out at once if you want to get more.
If you want to play pac-man, you can go to google.com and search for “google pac man” and you will get the result and select the first link and you will get the “Google Pac Man”.
Yes, you can play on your PC. You can play this game by using the keyboard button left-right and up-down buttons, or you can use Bluestacks.
In order to beat Pac-Man, you have to eat all the dots in the level and try to finish at one time without taking life. Once you have done that, the enemy will chase you. You need to lead them into the four corners of the level; they will freeze.
Wrapping Up: It Is Still Famous
Pac man doodle is one of the most famous arcade games in the world. From the 1980s to the 21st century, it has had a huge fan following in the game industry.
These facts about Pac-Man make this game more interesting. Hopefully, you will enjoy this article too.
Please let me know your words below the comment section. If you want to know more about games and the fun facts behind the games, you can visit our website also.
Read Also: