Seeing this message pop up on your screen – “Chrome has been blocked by your Windows Firewall” can irritate.
It is more irritating because your firewall does not exactly tell you why Google Chrome is accessing your network. This hampers your work and only creates more trouble for you.
Therefore, if you want to find the remedy to this problem, then you need to learn how to allow chrome to access the network in your firewall or antivirus settings.
To do so on Windows and Mac computers, there are various ways. To learn them, continue reading.
Methods To Allow Chrome To Access The Network In Your Firewall Or Antivirus Settings
To learn how to allow chrome to access the network in your firewall or antivirus settings, can follow three methods. These methods involve excluding Google Chrome from the list of potentially harmful or unauthorized lists in three places:
- Windows Firewall.
- Windows Defender.
- Third-Party Antivirus Software.
Read More: Ways to use Google analytics to find content ideas
Method 1: Add Chrome As An Exclusion To Your Windows Firewall Settings
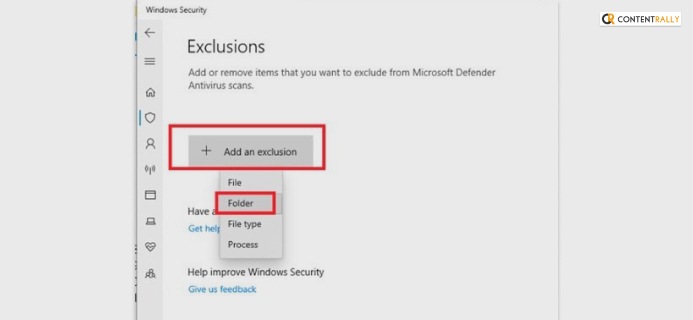
To add Chrome as an extension to your Windows firewall, follow these steps explained in order:
- Press both the Windows + R keys to open the Run menu.
- When the Run menu opens up, search for Control to open the Control Panel.
- In the control panel, click on System and Security.
- It will then show many options to you. Here, select Windows Defender Firewall.
- Click on the option called Allow an app to pass through the Firewall.
- When new options open up, select the option to Change Settings.
- A Yes prompt will open up. Accept by clicking on it.
- A new set of options will open up. Click on Allow other Apps.
- You will now get an option to Add Apps. Click on it.
- Here, you will be able to add the app Google Chrome from the Browse option. Click on it.
- In the browse menu, go to these folders in order:
C: > Program Files (x86) > GoogleChrome
- Open the folder to select the file called Chrome.exe.
- Click on the Add option.
- Another pop-up will appear on the screen. Select and tick mark both the options – Allow Access To Private Networks and Allow Access to Public Networks.
- To save all these changes, click on OK in the Control Panel.
Method 2: Add Chrome As An Exclusion To Your Windows Defender Settings
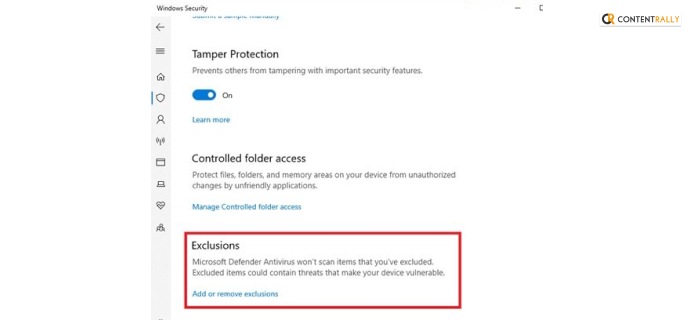
To exclude google Chrome from your Windows Defender Firewall, you need to follow these steps in order to learn how to allow chrome to access the network in your firewall or antivirus settings:
- Open the Start menu – you can do this by clicking on the Start icon in the taskbar or simply by clicking on the Windows key on your keyboard.
- Search for an option called Update and Security and click on it.
- Then, click on Open Windows Security.
- A panel with various options will open up on the left edge of the screen. Click on Virus and Threat Protection.
- Open up the Manage Settings option.
- Look for the Exclusions option by scrolling down through all the available options.
- Open the option called Add or Remove Extensions.
- Many other options will now open up. First, choose to Add an Exclusion.
- Click on Browse.
- Look for this folder in this order: C: > Program Files (x86) > GoogleChrome
- Select Chrome.exe from all the files in the folder.
- Click on Select Folder.
- Click on OK on the Windows Defender Firewall settings.
Method 3: Excluding Chrome As A Blocked Application From Your Antivirus Settings
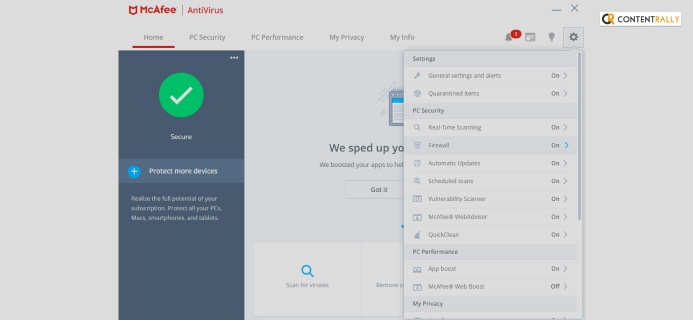
- Open your antivirus software.
- Go to its Settings.
- Click on an option called Exclusions.
- Look for the option named Allow Application Access to Network. Click on it.
- The Browse menu will open up. Look for this folder: C: > Program Files (x86) > GoogleChrome
- Click on Chrome.exe. It will be near the bottom of the page.
- Select Add or Allow option on your antivirus software settings.
Method 4: Allow Chrome To Access The Network In Your Firewall Or Antivirus Settings On A Mac
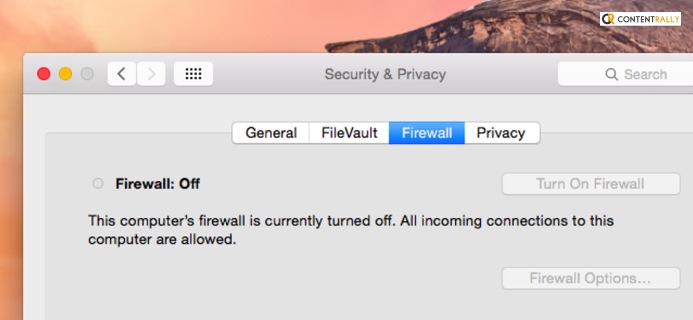
To learn how to allow chrome to access the network in your firewall or antivirus settings on Mac, you need to :
- Open Settings (click on the icon on the bottom of the screen that looks like an Apple).
- Go to System Preferences.
- Choose the option Security and Privacy.
- Choosing the tab above will open up the Firewall menu.
- Click on Firewall Options.
- Click on the “+” that will be at the bottom of the menu.
- The lists of all apps will open up. Browse and choose Google Chrome.
- Click on Add.
- In the end, click on OK.
Click Here To Read: Pros and Cons on Google Translation Accuracy
Frequently Asked Questions (FAQs):
Allowing Chrome access to your network in the firewall has remained the same as the process used for Windows 10. You need to go to your Firewall settings from the Start or Run menu to add Chrome as an exclusion manually.
Your firewall might be blocking Google Chrome because of any of the following reasons:
1. You are trying to open an unauthorized website using Google Chrome (primarily targeted toward pornographic websites and pirated torrent websites).
2. You downloaded Chrome from an unofficial third-party website.
You will not lose all your saved data on Chrome, like your starred bookmarks and saved passwords. This process will not tamper with your Chrome data in any way at all.
Yes, it’s safe to allow Chrome to have access to your networks through your firewall. However, this can be risky if you open unauthorized websites that Google does not verify.
Conclusion!
You must learn how to allow chrome to access the network in your firewall or antivirus settings.
This is important because you might face the problem of Chrome being blocked from your networks by your firewall. This can happen for many reasons, which your firewall will not specify.
To do so on Windows computers, you need to give Chrome access to your network by going through your Windows Firewall and Windows Defender security settings. You can also manually change the firewall settings of your antivirus application.
You can also do the same for Mac computers and a Macbook.
Read Also:






















